Attackers compromised up to 1500 companies during massive ransomware attack, which is now reported as one of the largest cyber attacks ever. Victims have been infected with REvil ransomware, which is similar to DarkSide ransomware used recently in Colonial Pipeline attack. However, this time, the deployed REvil ransomware was more obfuscated than versions observed in beginning of 2021. In this article, we will discuss the obfuscation techniques used by REvil in Kaseya incident.
First, after attack the attackers demanded $70 Million of ransom payment for universal decryptor. Later, they dropped to “only” $50M. Also, FBI has issued Statement on Kaseya Ransomware Attack and they started their own investigation.
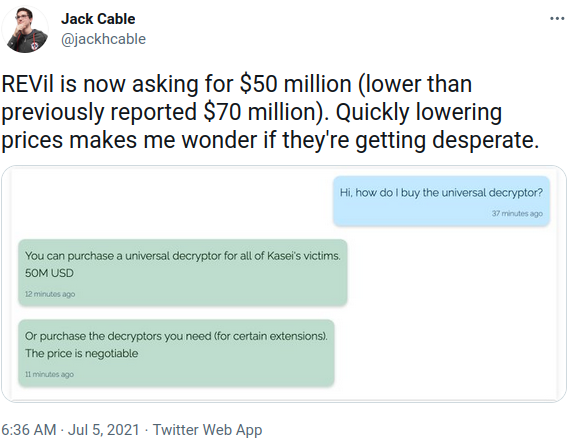
Fig. 1: REvil group asked $50M for universal decryptor. Source: Twitter
Dropper
The attackers deployed the program called agent.exe (VirusTotal, Any.Run). After execution, this program drops two files into %TEMP% directory, MsMpEng.exe and mpsvc.exe. Then, it executes MsMpEng.exe, which is legitimate Microsoft Malware Protection Antimalware Service Executable. This is older version, however, it still works and it is signed by Microsoft, too.
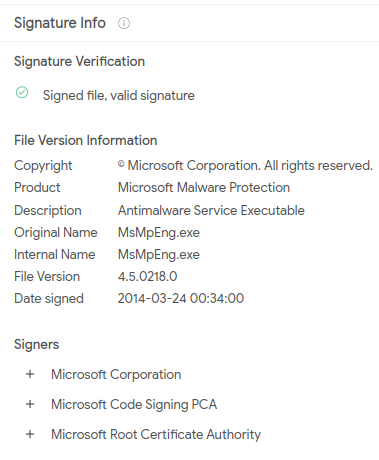
Fig. 2: Legitimate MsMpEng.exe file signed by Microsoft
This executable is prone to DLL hijacking. It means, that attackers can execute their malicious payload by side-loading DLL from the same directory - %TEMP% in this case. We can see this behavior in the aforementioned Any.Run analysis.
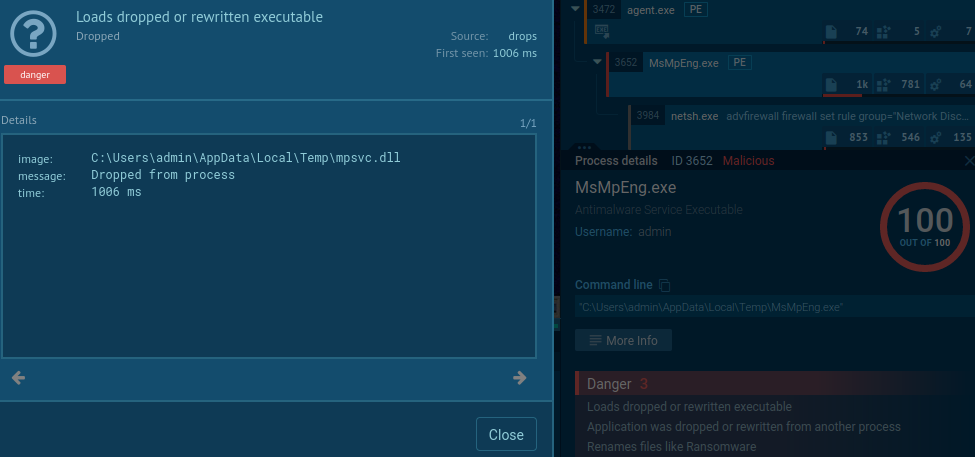
Fig. 3: DLL Side-Loading: malicious mpsvc.dll is loaded by MsMpEng.exe
Actually, dropper agent.exe is very simple. It contains two resources called MODLIS and SOFTIS. These resources are files to be dropped, the mpsvc.dll and MsMpEng.exe. After agent.exe drops these files, it executes the MsMpEng.exe which then loads malicious DLL file.
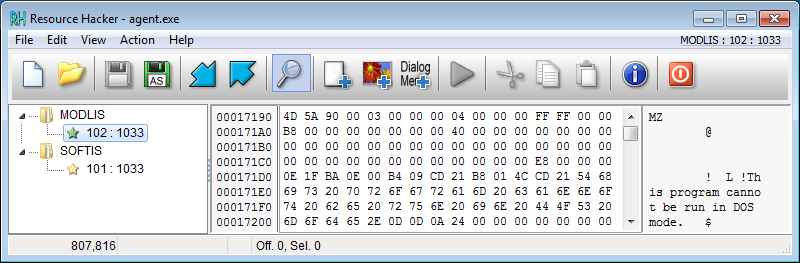
Fig. 4: Resources of agent.exe: MODLIS (mpsvc.dll) and SOFTIS (MsMpEng.exe)
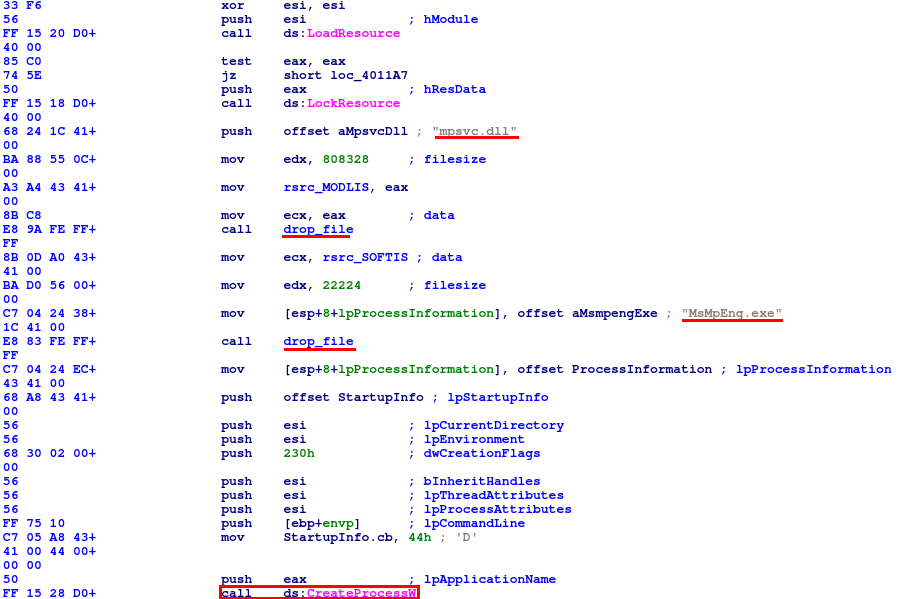
Fig. 5: agent.exe drops its resources MODLIS and SOFTIS and executes MsMpEng.exe
Note: dropped file mpsvc.dll is slightly larger (808328 B) than the MODLIS resource (807816 B). The dropper writes more data to the mpsvc.dll file. While the appended data are only zeroes, this padding affects payload hashes.
Malicious DLL
Malicious DLL contains obfuscated REvil ransomware. First, its exported function ServiceCrtMain creates new thread in which executes a “loader” function.
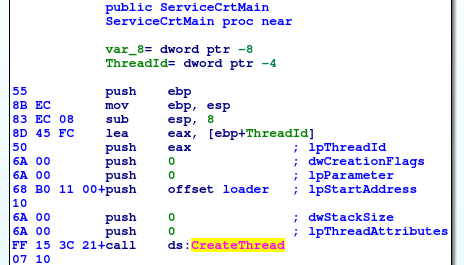
Fig. 6: ServiceCrtMain function in malicious DLL creates new thread.
Loader function decrypts the payload encrypted with RC2 in CFB mode. It uses the embedded OpenSSL library for the cryptography operations. Encrypted payload with obfuscated decryption key is stored in data section. Before decrypting the payload, loader deobfuscates the decryption key. Obfuscation is simple, i-th character of the key is xored with i and the number derived from the obfuscated key.
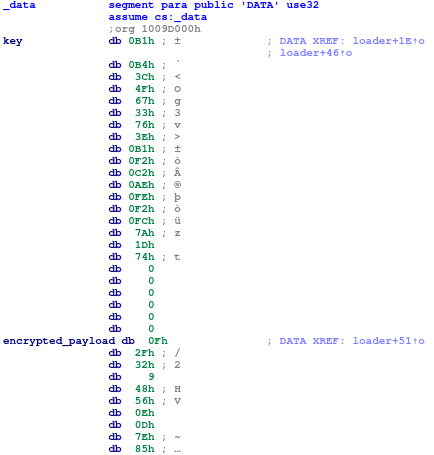
Fig. 7: Encrypted payload and decryption key in data section of loader
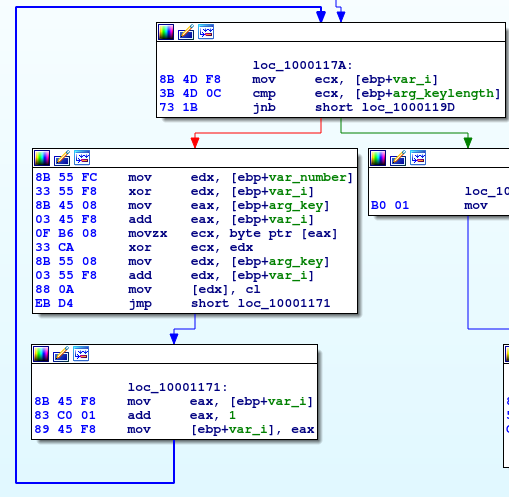
Fig. 8: Deobfuscation of the key by xoring characters
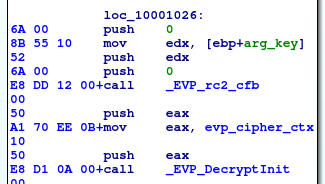
Fig. 9: Loader uses embedded OpenSSL’s RC2 for decrypting the payload
When payload (130048 bytes) is decrypted, the loader maps it into memory (CreateFileMapping) with PAGE_EXECUTE_READWRITE access rights, so it can write, modify and execute data in this memory area. The decrypted payload contains valid (shell)code and this code is executed then. Also, the loader passes the pointers to LoadLibrary and GetProcAddress functions to the executed shellcode.
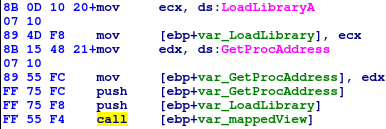
Fig. 10: Loader executes the decrypted payload
Decrypted Payload
The decrypted payload (or shellcode) is another layer of obfuscation. It contains packed version of REvil ransomware. It is interesting that despite the malicious nature, this payload (shellcode) is not detected by any of the antivirus engines on VirusTotal. Even couple days after the massive attack on Kaseya, and the obfuscated artifact with the REvil ransomware used in this attack is still not detected.
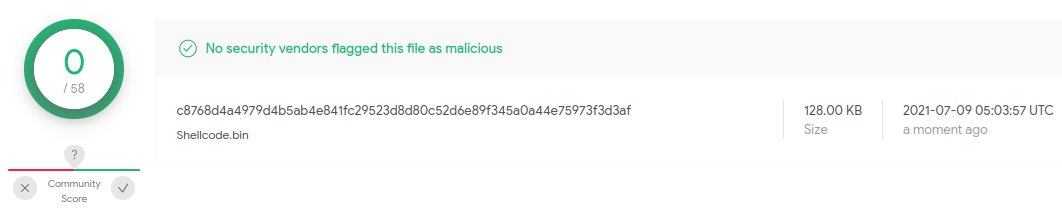
Fig. 11: Decrypted payload with obfuscated REvil ransomware is not detected by antiviruses
The unpacker stub allocates another memory and sets its protection to read, write and execute (ERW flags in Fig. 13). Now there are two memory regions with ERW protection - the first is for current stage with shellcode and unpacker stub, the second is a destination for unpacked payload with REvil ransomware.
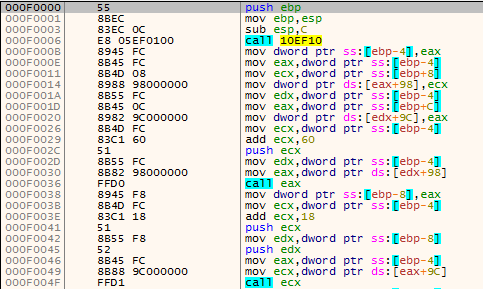
Fig. 12: Start of the unpacker stub in decrypted payload
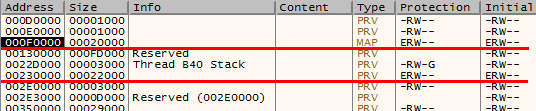
Fig. 13: Memory regions with execute-read-write protection for shellcode and unpacked REvil
Then, after the unpacking, the execution flow is redirected to the unpacked REvil ransomware.
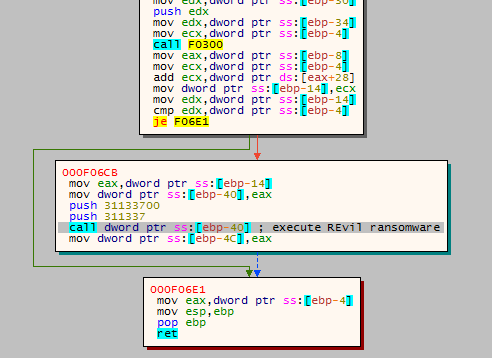
Fig. 14: End of the unpacker stub - call of the unpacked REvil ransomware
Unpacked REvil ransomware
The unpacked REvil ransomware is the PE file, but with partially cleaned DOS and NT header. MZ and PE signatures are removed as well as section names. However, most of the fields are present, e.g. Major and Minor Operating System Version (in this case NT 5.1, which means Windows XP), address of entry point (0x4883), which is also the place where unpacker stub redirected execution flow after unpacking.
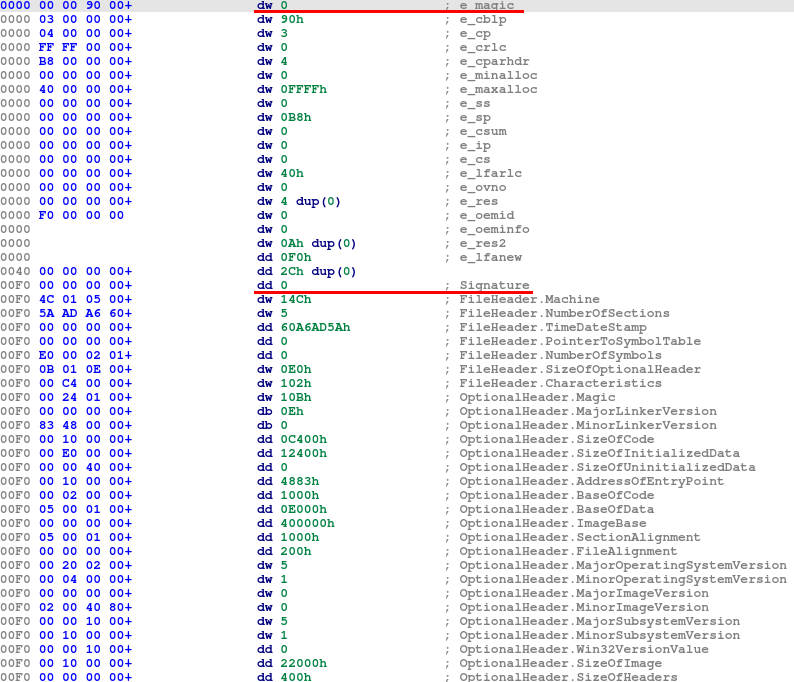
Fig. 15: Partially cleaned headers of REvil Portable Executable file - MZ and PE signatures are missing
Again, it is interesting that this unpacked version of REvil ransomware dumped from the memory is detected only by 2 antiviruses out of 59 on VirusTotal - one week after the attack on Kaseya happened.
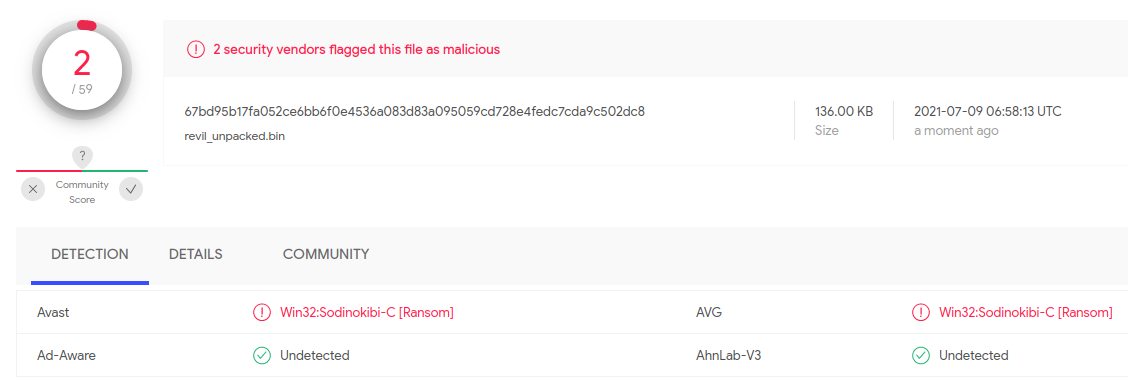
Fig. 16: Dumped and deobfuscated REvil ransomware has very low detection ratio 2/59
At the entry point, there is a pretty standard REvil ransomware as we observed few months ago. Simple start routine with two calls, decrypting the config, check for double run, etc.
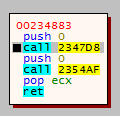
Fig. 17: Entry point of REvil ransomware
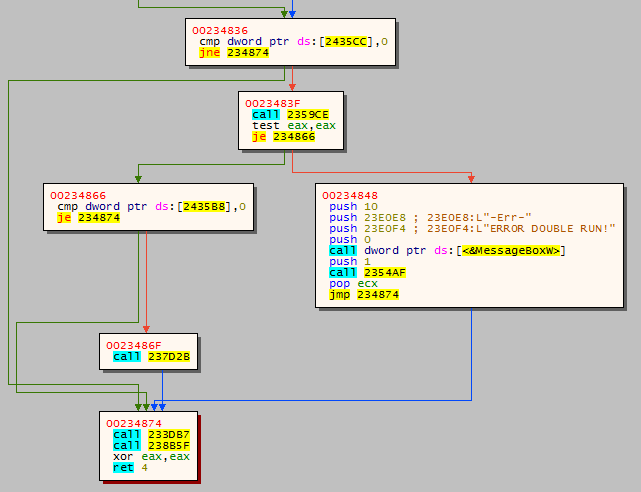
Fig. 18: Check if there is another instance of ransomware already running
REvil configuration
The configuration of REvil ransomware is encrypted by RC4. Encrypted configuration is stored in specific section (often called .cfg). Decryption key is stored in this section, too.
Fig. 19: Decryption key and encrypted REvil configuration
After decryption, the configuration is in JSON format and it contains various settings of REvil ransomware. We discussed more about REvil’s configuration and its similarities with DarkSide ransomware in our previous analysis.
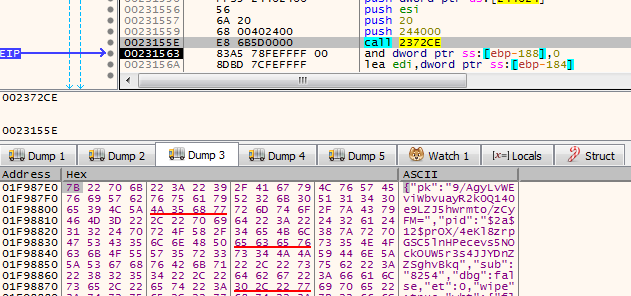
Fig. 20: Decrypted JSON configuration of REvil ransomware
Configuration contains template for ransom note, too. It is encoded in Base64 and uses placeholders to be replaced with the values related to the victim.
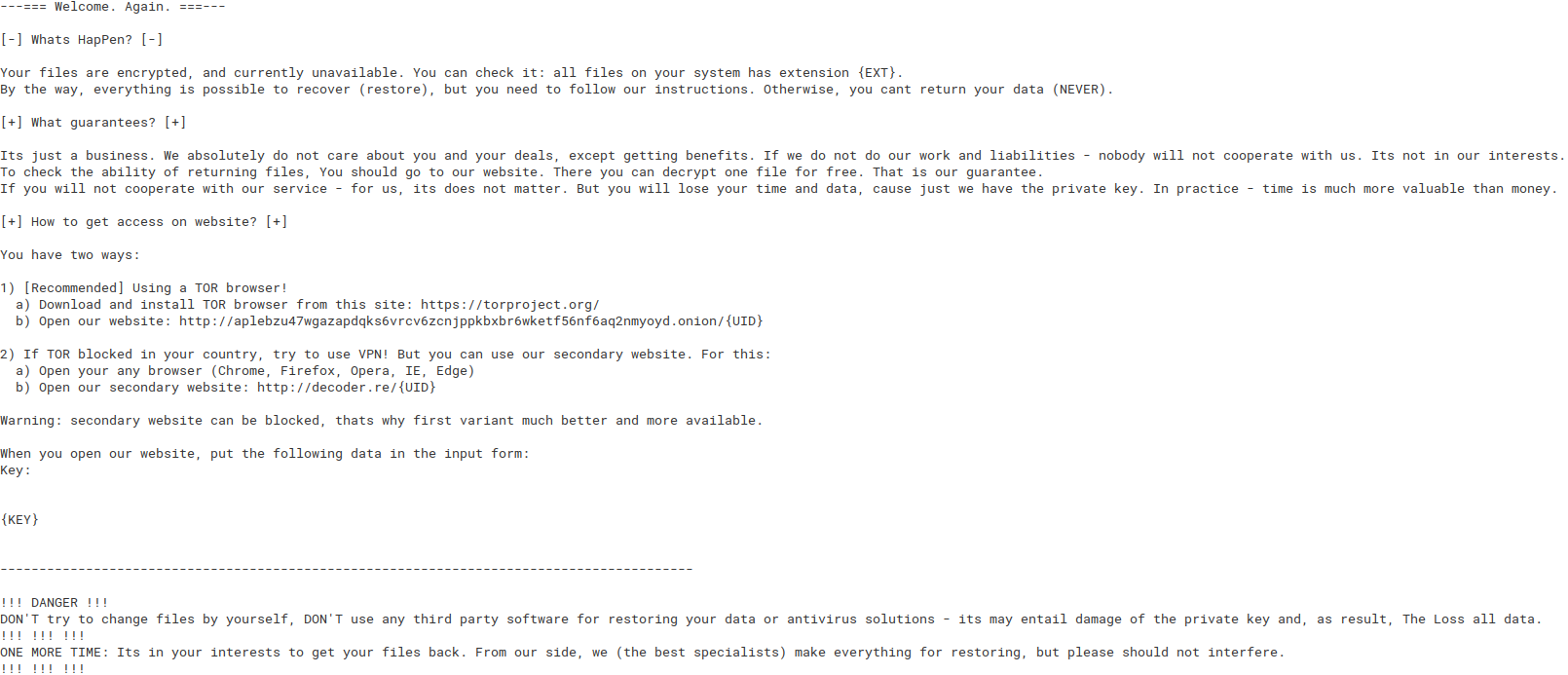
Fig. 21: REvil ransomnote template
REvil analysis highlights
REvil uses combination of symmetric and asymmetric encryption involving multiple public and private keys. It is due to the nature of its affiliate system. So, there are specific keys for operators, affiliates and infected systems. For further reading on this topic there is an excellent Twitter thread by Fabian Wosar. This thread also incudes an example of what data victims paste to the attackers from REvil ransomnote referred as {KEY} in the ransomnote template on Fig. 21.
When executed, REvil ransomware changes device password and sets computer to automatically log in. In the analyzed sample, this password is “DTrump4ever”, as is depicted in Fig. 22.
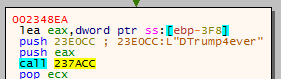
Fig. 22: REvil sets a new device password
However, in case of analyzed sample it has no efect, because boot manager is encrypted, too. Therefore, after reboot, only error message is displayed and device is not able to boot.
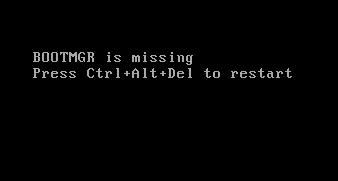
Fig. 23: REvil damaged boot manager
Conclusion
We analyzed execution flow of REvil ransomware used in recent cyber attack on Kaseya, which affects hundreds of victims. The ransomware sample has been protected by multiple layers of obfuscation and encryption. Even one week after attack, some of the antivirus evasion techniques are quite successful, when final ransomware unpacked in memory and its packed version are almost undetected by antiviruses.
We successfuly defeated the obfuscation and we extracted REvil’s configuration and ransomnote template, which are now available on our GitHub repository.
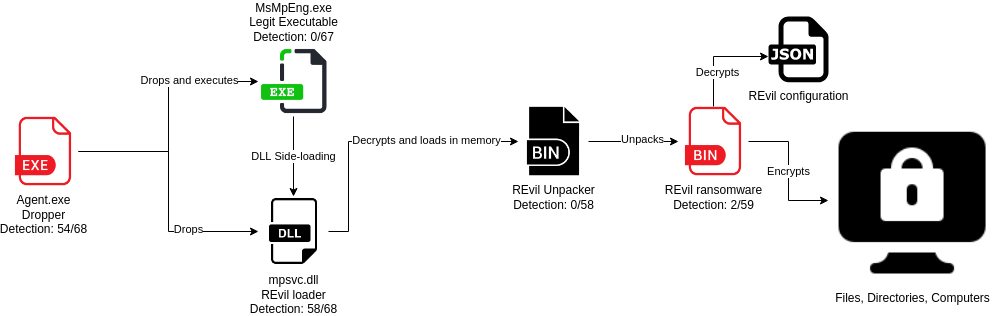
Fig. 24: Execution of REvil ransomware
References
- CNN article about Kaseya ransomware attack
- Attackers demandeded $50 Million
- FBI Statement on Kaseya Ransomware Attack
- ATT&CK MITRE T1574.002: Hijack Execution Flow: DLL Side-Loading
- DarkSide vs. Revil/Sodinokibi Similarities
- Twitter thread by Fabian Wosar about REvil cryptoraphy
- IstroSec’s GitHub repository with extracted REvil’s configurations and ransomnote templates
Samples and IOCs
- agent.exe dropper
- Any.Run analysis
- filesize: 912264 bytes
- MD5: 561cffbaba71a6e8cc1cdceda990ead4
- SHA256: d55f983c994caa160ec63a59f6b4250fe67fb3e8c43a388aec60a4a6978e9f1e
- MsMpEng.exe
- legitimate Microsoft Malware Protection Antimalware Service Executable
- signed by Microsoft
- dropped by agent.exe
- be careful of false positives, following hashes are legitimate, not malicious
- filesize: 22224 bytes
- MD5: 8cc83221870dd07144e63df594c391d9
- SHA256: 33bc14d231a4afaa18f06513766d5f69d8b88f1e697cd127d24fb4b72ad44c7a
- mpsvc.dll
- malicious payload with obfuscated REvil ransomware dropped by agent.exe
- dropped file:
- filesize: 808328 bytes
- MD5: a47cf00aedf769d60d58bfe00c0b5421
- SHA256: 8dd620d9aeb35960bb766458c8890ede987c33d239cf730f93fe49d90ae759dd
- file from resource:
- filesize: 807816 bytes
- MD5: 7ea501911850a077cf0f9fe6a7518859
- SHA256: e2a24ab94f865caeacdf2c3ad015f31f23008ac6db8312c2cbfb32e4a5466ea2
- decrypted payload of mpsvc.dll/shellcode
- contains packed REvil ransomware
- filesize: 131072 bytes
- MD5: 3ad14947002e57887b82643d729c21ae
- SHA256: c8768d4a4979d4b5ab4e841fc29523d8d80c52d6e89f345a0a44e75973f3d3af
- unpacked REvil ransomware
- filesize: 139264 bytes
- MD5: f356f999ccc35d972453ffc15cb18440
- SHA256: 67bd95b17fa052ce6bb6f0e4536a083d83a095059cd728e4fedc7cda9c502dc8