DarkSide Ransomware is a very hot topic now, especially after the Compromise of Colonial Pipeline networks, which has been investigated by FBI, too. It caused so serious problems that even hackers said that they “didn’t mean to create problems”. However, DarkSide ransomware is not something completely new, and it is similar to the infamous Revil/Sodinokibi ransomware. In this post, I would like to highlight some significant similarities between newer samples of both ransomwares with insights about DarkSide victims based on custom ransom notes.
DarkSide Ransomware Analysis
Originally, I intended to write post about DarkSide ransomware analysis, but couple of days before my intent FireEye published their great threat research.
For now, it is important for this post that DarkSide ransomware is written in C and it is configurable. It supports file encryption on fixed, removable and network drives. It also supports beaconing to C2 server and persistence mechanism. For more details, please refer to the abovementioned analysis by FireEye.
DarkSide samples offers highly customizable builds via the affiliate program. In the wild, I observed lot of different samples, some of them have been packed with UPX packer, VMProtect or with custom packers. There is also at least one signed sample, which means that it is considered as safe program by many security solutions - this signed sample will be discussed later. Filesize of the observed DarkSide ransomware samples differs between 14 kB and 2 MB. Majority of the samples is approximately 40-60 kB in size.
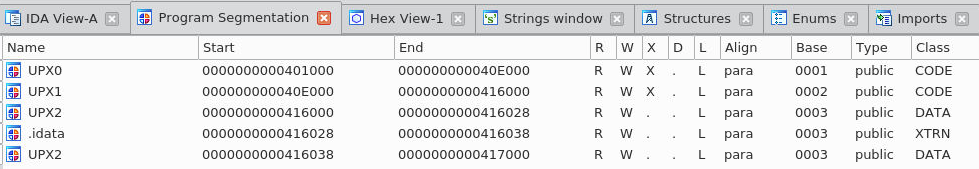
Fig. 1: DarkSide sample packed with UPX packer
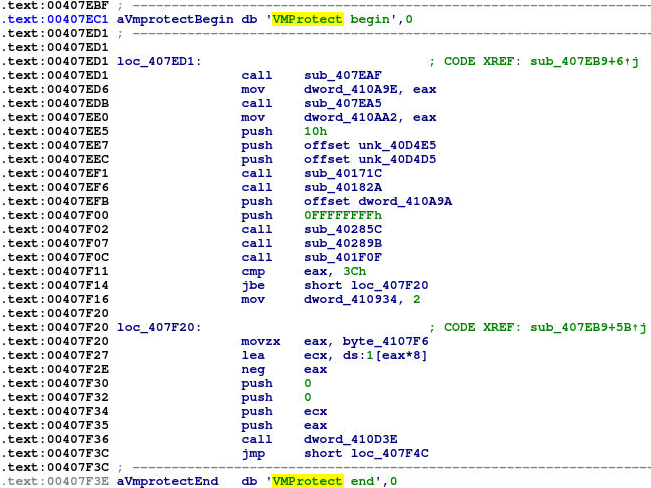
Fig. 2: DarkSide sample with VMProtect markers
Two another interesting quick finds are that DarkSide performs check for installed systen languages/keyboards, and if there is installed keyboard related to Russian-speaking country, the ransomware will not encrypt files.
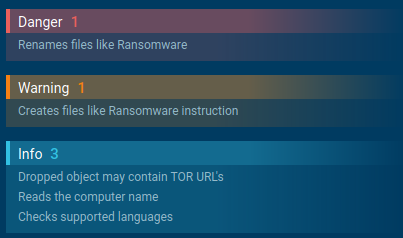
Fig. 3: DarkSide checks supported languages
Second fact is that DarkSide deletes volume shadow copies (as most of the ransomwares), but it has different behavior when it is executed on 64-bit Windows (WOW64) and on 32-bit system. On 32-bit systems, it uses COM and WMI. On 64-bit system it executes powershell with obfuscated command (see Fig. 4). After deobfuscation, the executed command is
Get-WmiObject Win32_Shadowcopy | ForEach-Object {$_.Delete();}
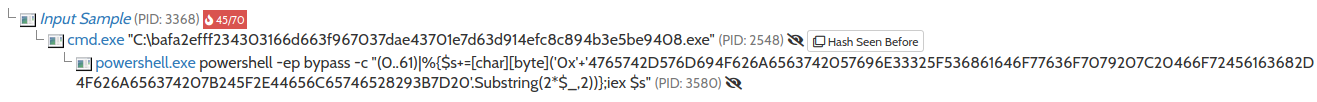
Fig. 4: Obfuscated PowerShell command deletes volume shadow copies
DarkSide vs. Revil/Sodinokibi Similarities
Configuration
When I saw extracted configuration of DarkSide ransomware, I immediately recognize overlapping with the Revil/Sodinokibi configuration. This is clearly visible in the ignored file extensions, files and directories, and in lists of processes to terminate and services to stop. Some of these options are identical with Revil, while others are very similar, as we can see in the pictures below.
Both DarkSide and Revil/Sodinokibi supports lists of ignored (whitelisted in case of Revil) files and processes/services to stop. While the format is very different (encrypted binary blob in DarkSide and encrypted json in Revil), the content overlaps in many options.
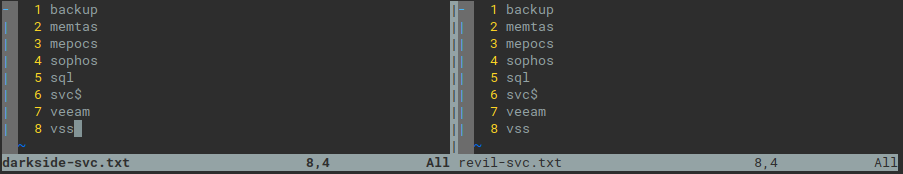
Fig. 5: Services to stop - DarkSide vs Revil
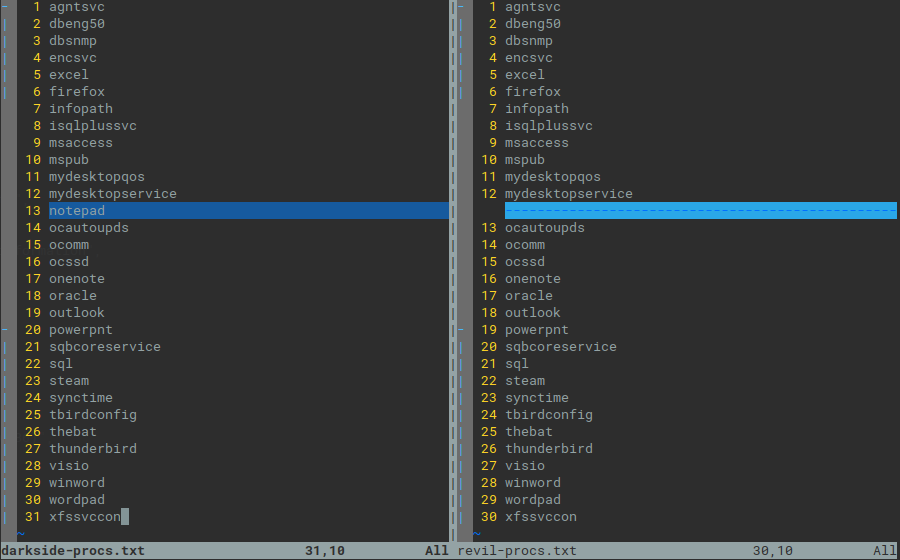
Fig. 6: Processes to terminate - DarkSide vs Revil
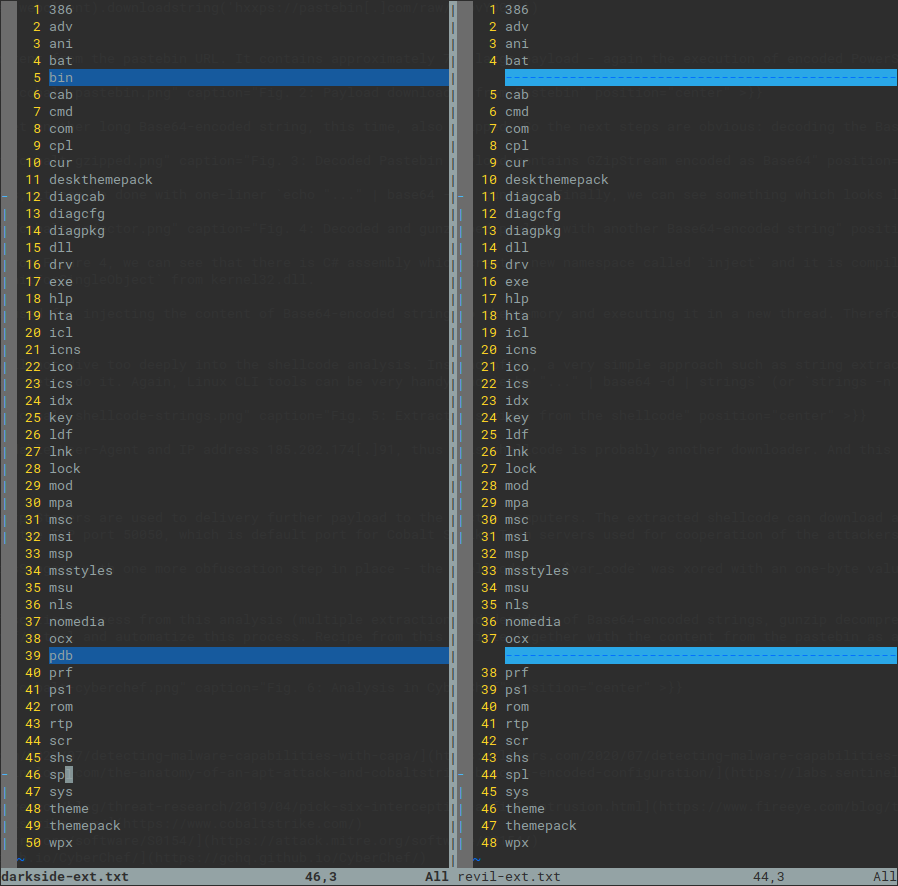
Fig. 7: Ignored file extensions - DarkSide vs Revil
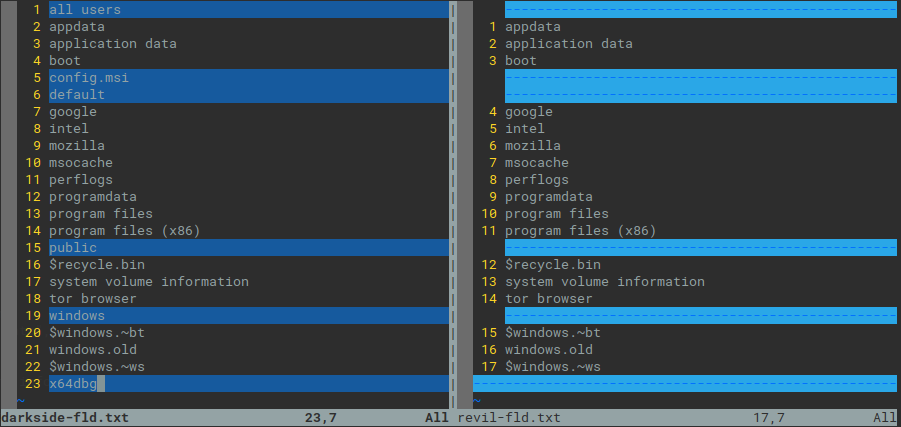
Fig. 8: Ignored folders and locations - DarkSide vs Revil
This comparison is based on configuration of DarkSide ransomware samples docummented in FireEye report (older versions observed earlier this year and in May 2021) and on configuration extracted from Revil/Sodinokibi samples observed in February and March 2021.
Cryptography
Both ransomware families use combination of asymmetric and symmetric cryptography for file encryption. In case of Revil/Sodinokibi it is Salsa20 with key derived during complicated key-derivation process based on Curve25519. In case of DarkSide ransomware it is Salsa20 with randomly generated key and encrypted with RSA-1024. Moreover, the Salsa20 implementation in Revil is based on public domain, C implementation by D.J. Bernstein. For more information about Revil encryption, see this Intel471’ analysis.
Therefore, it seems that implementation of DarkSide symmetric cryptography remains, while assymmetric cryptography has been simplified.
Affiliate System
Nowadays there are ransomware gangs which adopt affiliate system. They offer ransomware as a service (RaaS). Their partners are usually able to create custom builds/configurations of the ransomware and maintain and monitor their campaigns. In both cases (Revil and DarkSide), the affiliate program is offered on Russian-speaking forums, namely Exploit and XSS. Based on similarity of the configurations and ransomnotes, it seems that there is a significant overlapping between affiliates of Revil and DarkSide. This was also observed by several researchers and companies.
Ransomnote
There are many samples of DarkSide and Revil ransomwares which were uploaded to public malware analysis services such as VirusTotal, Any.Run, Hybrid-Analysis and others. Using the advanced filters and threat intelligence approach it is possible to find lot of ransomnotes dropped by both DarkSide and Revil ransomwares. Armed with such a collection of ransomnotes and dates when the associated samples have been first seen in the wild, we can follow the evolution of the ransomnotes’ content.
And we can see that DarkSide ransomnotes are very similar to Revil ransomnotes. There are many overlaps of common sentences and phrases, instructions, format, etc. However, there are also differences, based mainly on customization of DarkSide ransomnote for the particular victims. On the other hand, it still seems that Revil’s ransomnotes have been used as a template for DarkSide ransomnote. See Figures 9 and 10, especially the section names and the content of the section “How to get access on website?”
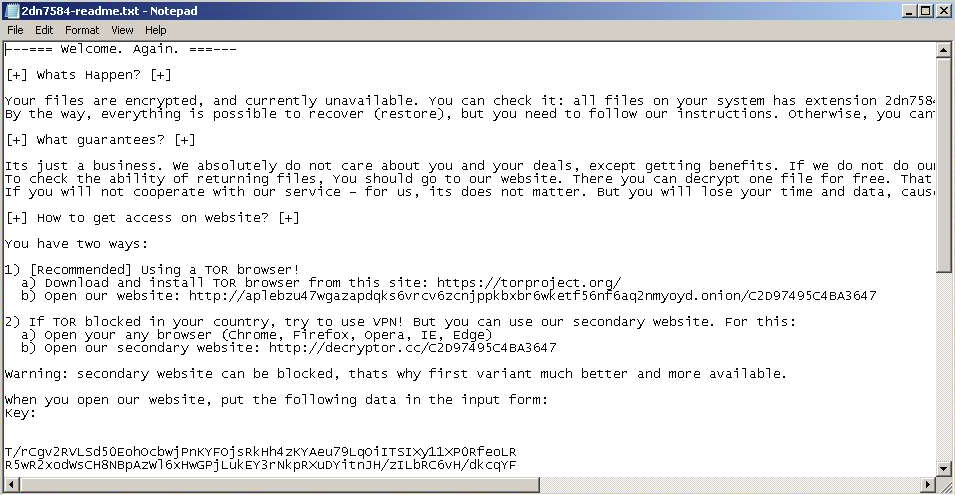
Fig. 9: Revil Ransomnote, victim: N/A, first submission: 2020-08-18
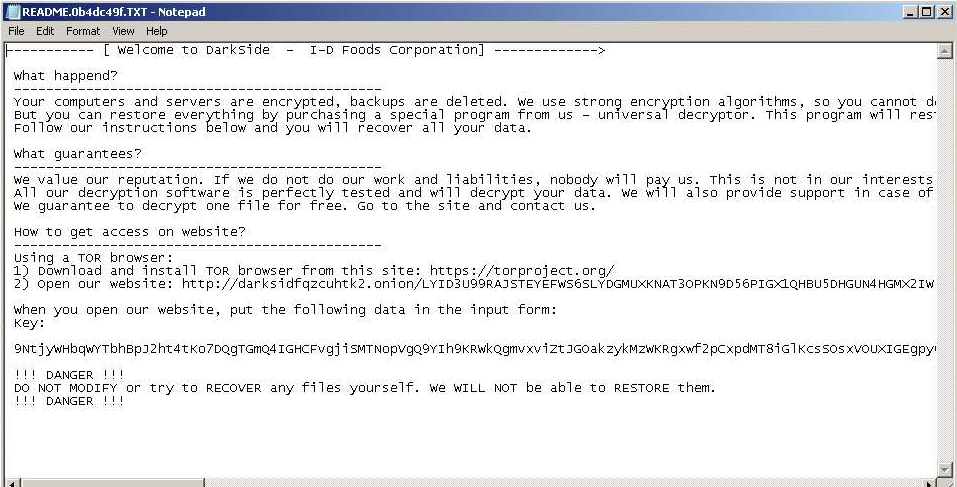
Fig. 10: DarkSide Ransomnote, victim: I-D Foods Corporation, first submission: 2020-09-03
Then DarkSide ransomnotes evolved with adaptation per their victims and stolen and encrypted data. E.g. there are explicit enumerations of what kind and what amount of data have been leaked. There are also personalized links to DarkSide blogs, in many cases, these personalized links contain also the name of victim, as we can see below.
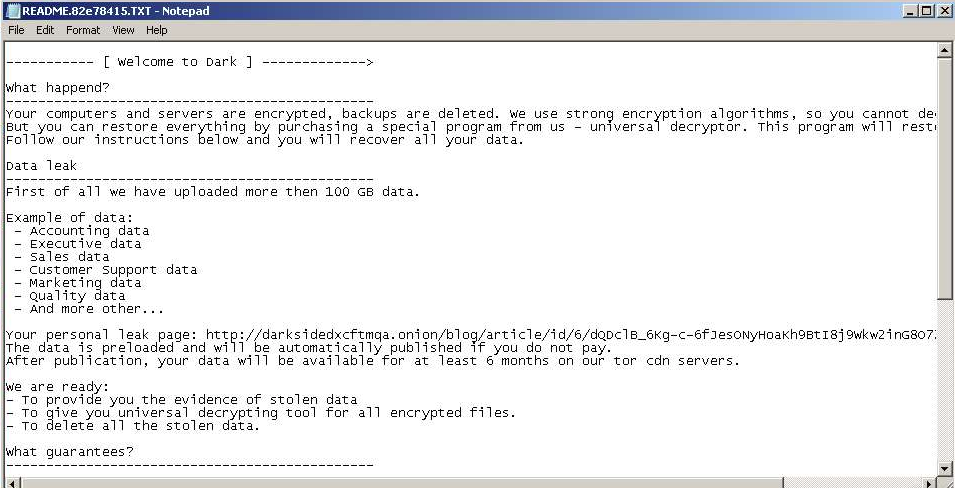
Fig. 11: DarkSide Ransomnote, victim: N/A, first submission: 2020-09-03
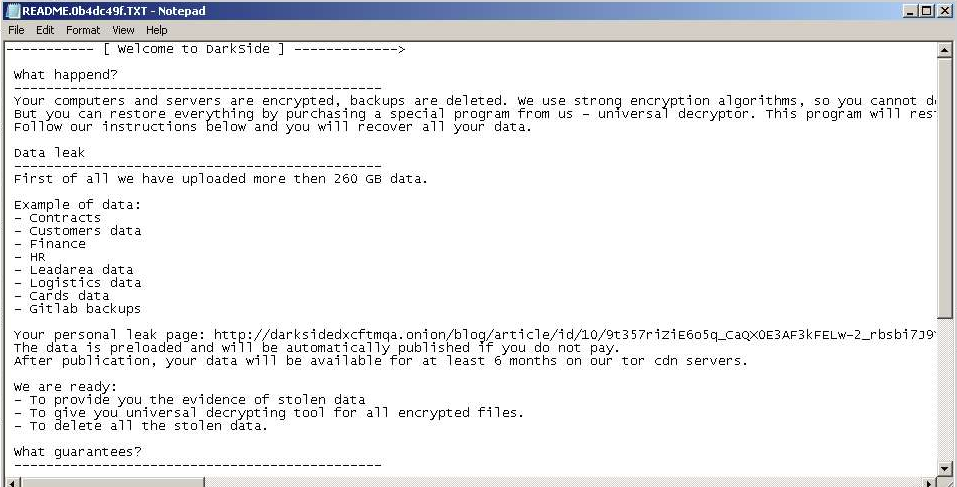
Fig. 12: DarkSide Ransomnote, victim: N/A, first submission: 2020-10-03
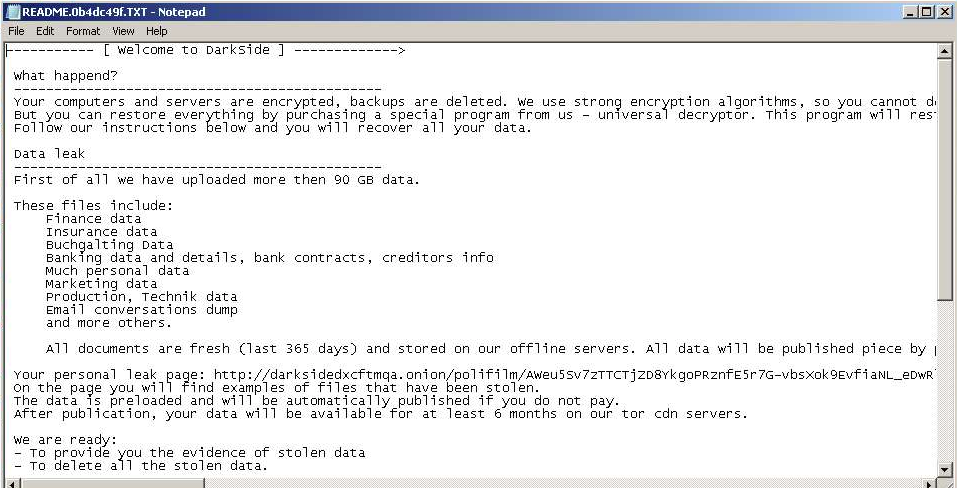
Fig. 13: DarkSide Ransomnote, victim: Polifilm, first submission: 2020-12-23
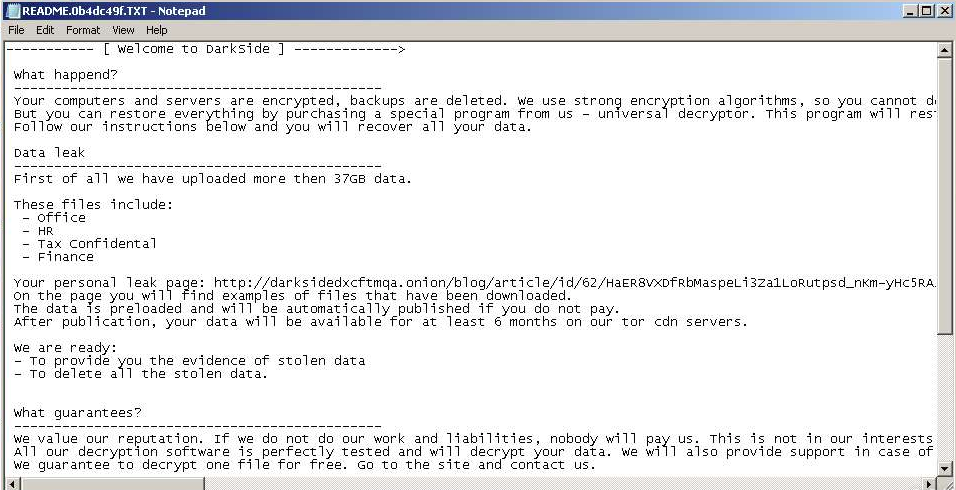
Fig. 14: DarkSide Ransomnote, victim: N/A, first submission: 2021-01-29
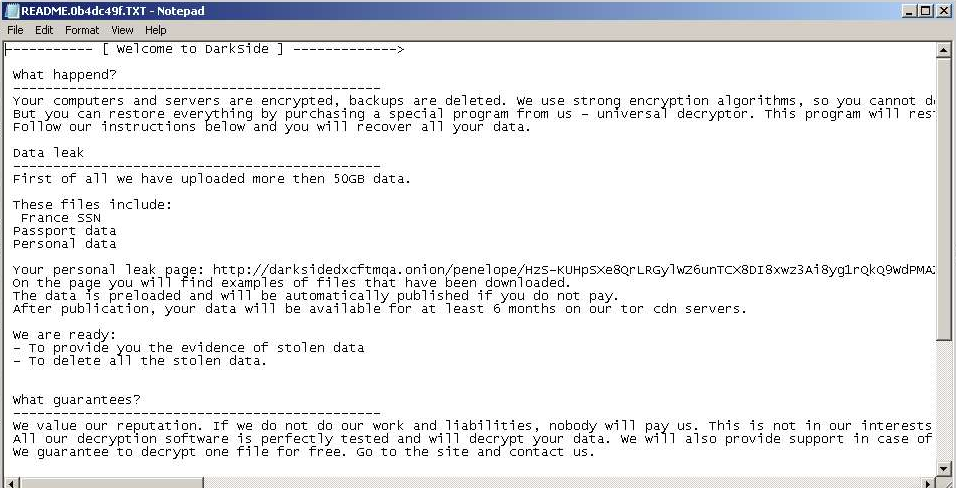
Fig. 15: DarkSide Ransomnote, victim: Penelope, first submission: 2021-02-01
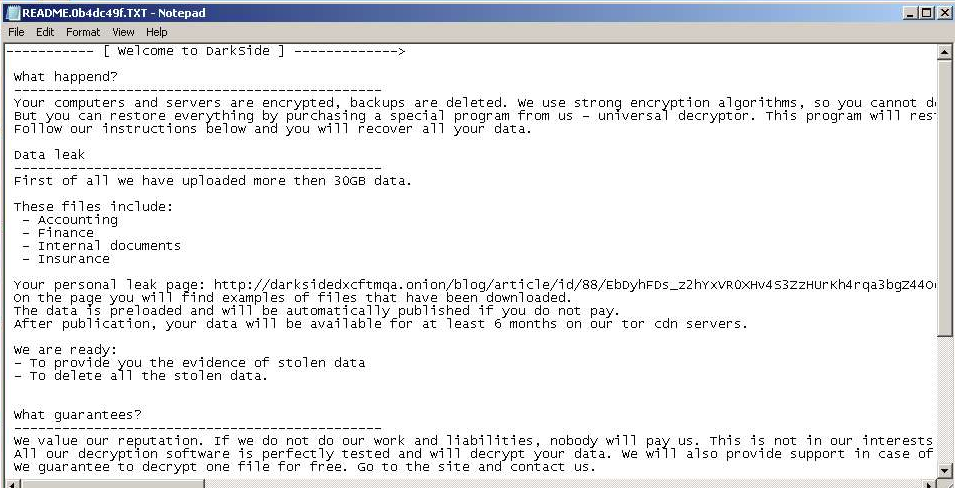
Fig. 16: DarkSide Ransomnote, victim: N/A, first submission: 2021-02-17
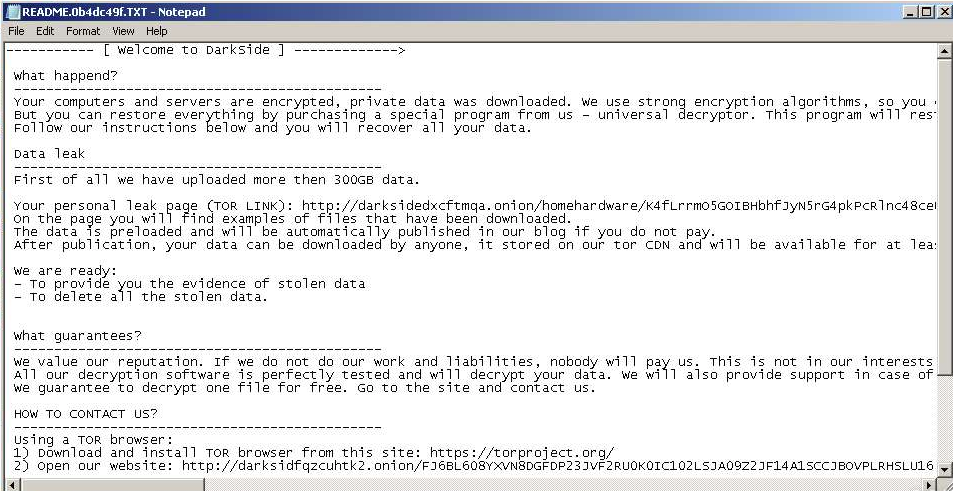
Fig. 17: DarkSide Ransomnote, victim: HomeHardware, first submission: 2021-02-18
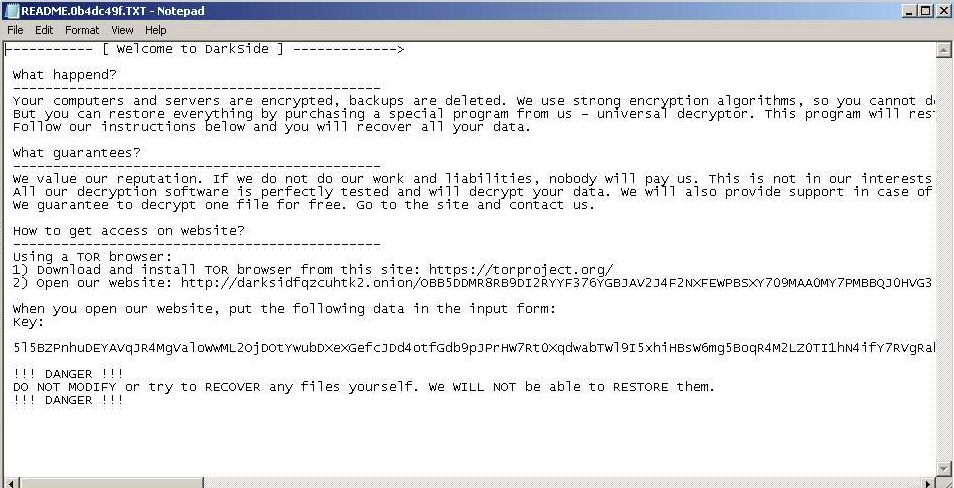
Fig. 18: DarkSide Ransomnote, victim: N/A, first submission: 2021-02-23
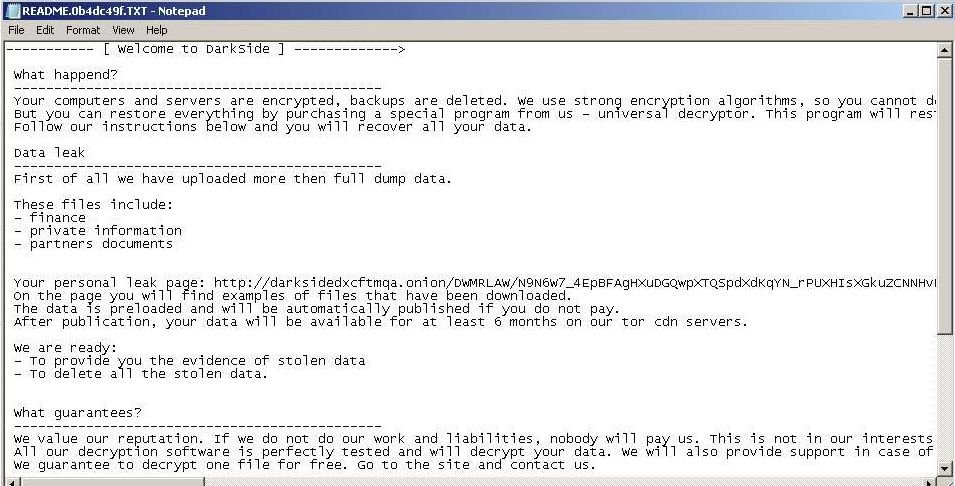
Fig. 19: DarkSide Ransomnote, victim: DWMR, first submission: 2021-03-06
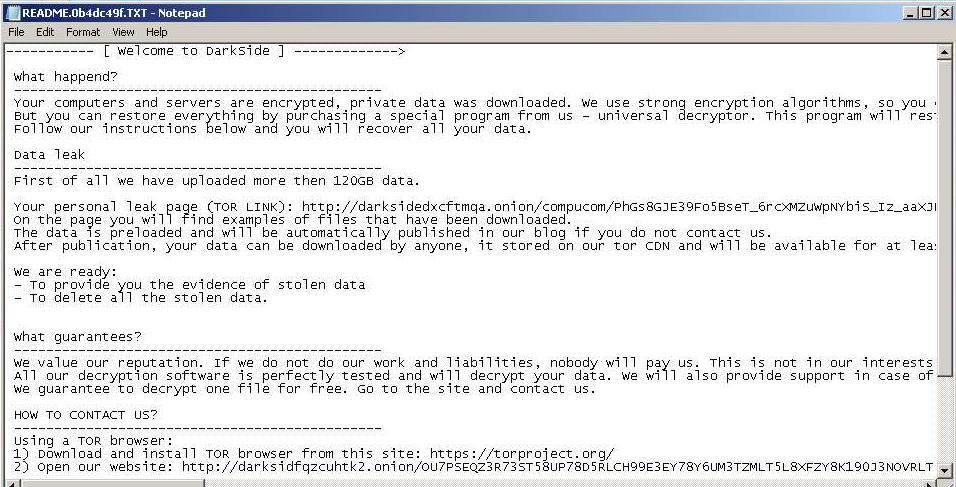
Fig. 20: DarkSide Ransomnote, victim: CompuCom, first submission: 2021-04-21
Victims
Based on ransomnotes above, we can summarize information about DarkSide’s victims. Of course, those are only examples and there are much more victims. Probably hundreds - just see the incrementing ID parameter in the above screenshots of older DarkSide ransomnotes, before they changed the personal link format.
Information extracted from ransomnotes examples is summarized in the table below. There are wide range of victims and industries, including tech, communications, law and food companies.
| Victim | Leaked data | Data Volume | Ransomnote | 1st submission of ransomware sample |
|---|---|---|---|---|
| I-D Foods Corporation | N/A | N/A | Fig. 10 | 2020-09-03 |
| N/A | Accounting Executive Sales Customer support Marketing Quality | 100 GB | Fig. 11 | 2020-09-03 |
| N/A | Contracts Customer data Finance HR Leadarea data Logistics data Cards data Gitlab backups | 260 GB | Fig. 12 | 2020-10-03 |
| Polifilm | Finance Insurance Accounting Banking data Persona data Marketing Production data Email dumps | 90 GB | Fig. 13 | 2020-12-23 |
| N/A | Office HR Tax Confidential Finance | 37 GB | Fig. 14 | 2021-01-29 |
| Penelope | France SSN Passport data Personal data | 50 GB | Fig. 15 | 2021-02-01 |
| N/A | Accounting Finance Internal docs Insurance | 30 GB | Fig. 16 | 2021-02-17 |
| Home Hardware | N/A | 300 GB | Fig. 17 | 2021-02-18 |
| Duggins Wren Mann & Romero (DWMR Law) | Finance Private info Partners docs | Full dump | Fig. 19 | 2021-03-06 |
| CompuCom | N/A | 120 GB | Fig. 20 | 2021-04-21 |
| Colonial Pipeline | N/A | 100 GB | N/A | 2021-05-06 (Data leak) |
Among the incidents and cases in the table above, I would like to emphasize two of them (besides Colonial Pipeline incident, which was already discussed almost everywhere).
Signed malware
The first one is the hack of Home Hardware. DarkSide ransomware sample called homie.exe or MicSwitch.exe (Any.Run analysis, VirusTotal report) is signed and the signature is still valid. At least, VirusTotal reports it as the valid signature.
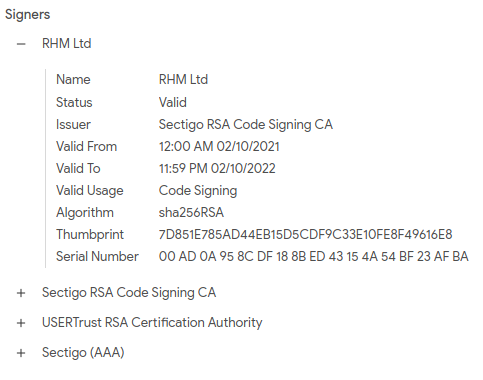
Fig. 21: Signed DarkSide Ransomware sample
The code signing certificate was issued to RHM Ltd on 2021-02-10, only two days after the creation (compilation) timestamp of the sample and 8 days before first submission to VirusTotal. The question is, if this is a legitimate certificate misused by attackers, or, if it is a certificate issued only for this malicious purpose. Maybe the certificate was requested by attackers themselves on behalf of RHM Ltd, but this is only a speculation.
Regarding RHM Ltd, there are at least two RHM Ltd companies, the first is a consumer food manufacturer, the second is a healthcare marketing company. We can extract more information from the code signing certificate and from the malware sample and we will see the address Premier House Centrium Business Park St Albans. Thus the certificat was issued to the the consumer food manufacturer company. Moreover, there is visible yahoo email address [email protected], which is definitely not the best practise to use freemail address for certificates requests…
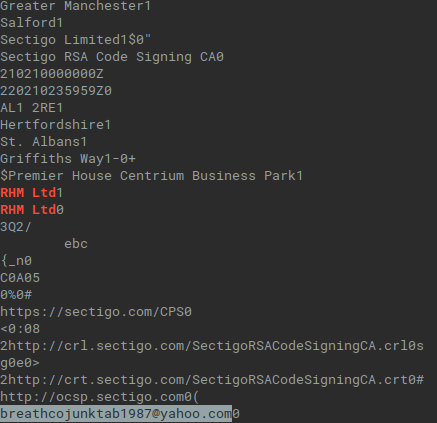
Fig. 22: Extracted strings related to the code-signing certificate
DarkSide website, victims and partners
The second case is related to Polifilm incident. Especially this analysis on Any.Run is interesting. Analysts visited the DarkSide website accessible via TOR and now we can use this analysis as a quick walkthrough of what we can find on similar RaaS portals. Of course, the obvious website for uploading the key from ransomnote and computing the demanded ransom amount. In this case, $ 4,000,000 in XMR (Monero).
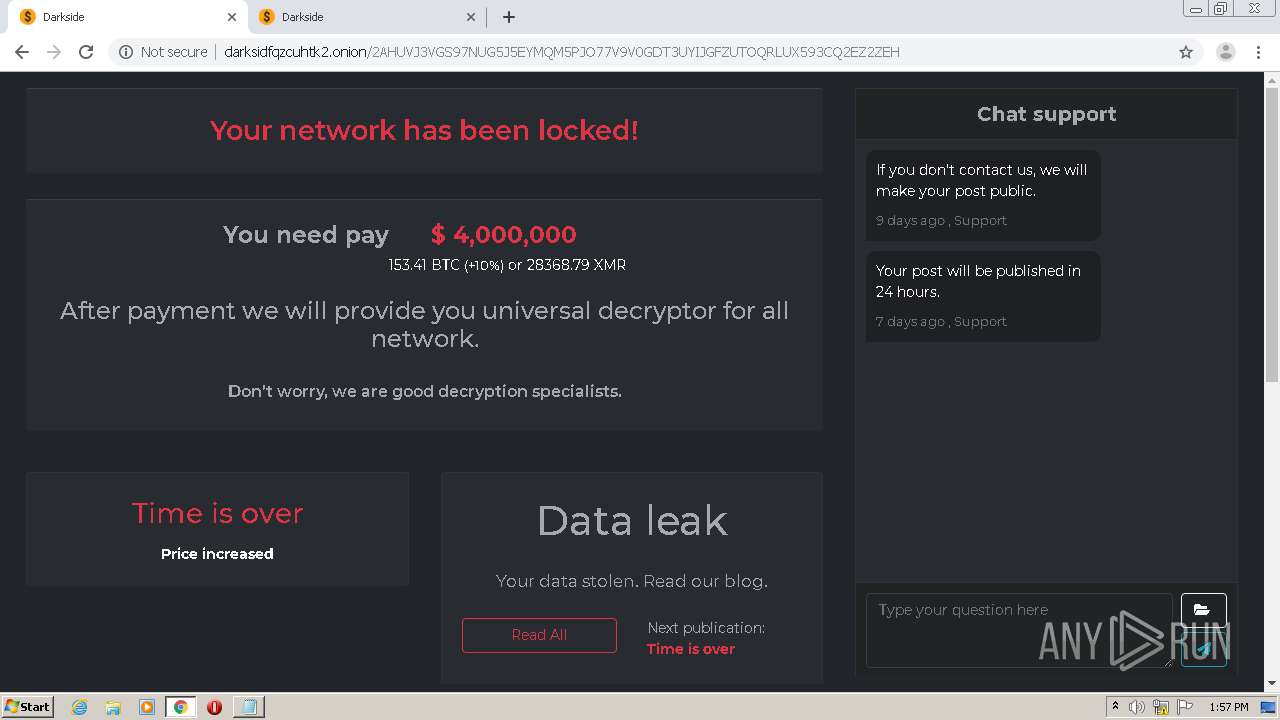
Fig. 23: DarkSide portal with payment info
Next, as an example, how can look ransomware blog about victims (or Hall of Shame), this page was also accessed during the Any.Run analysis.
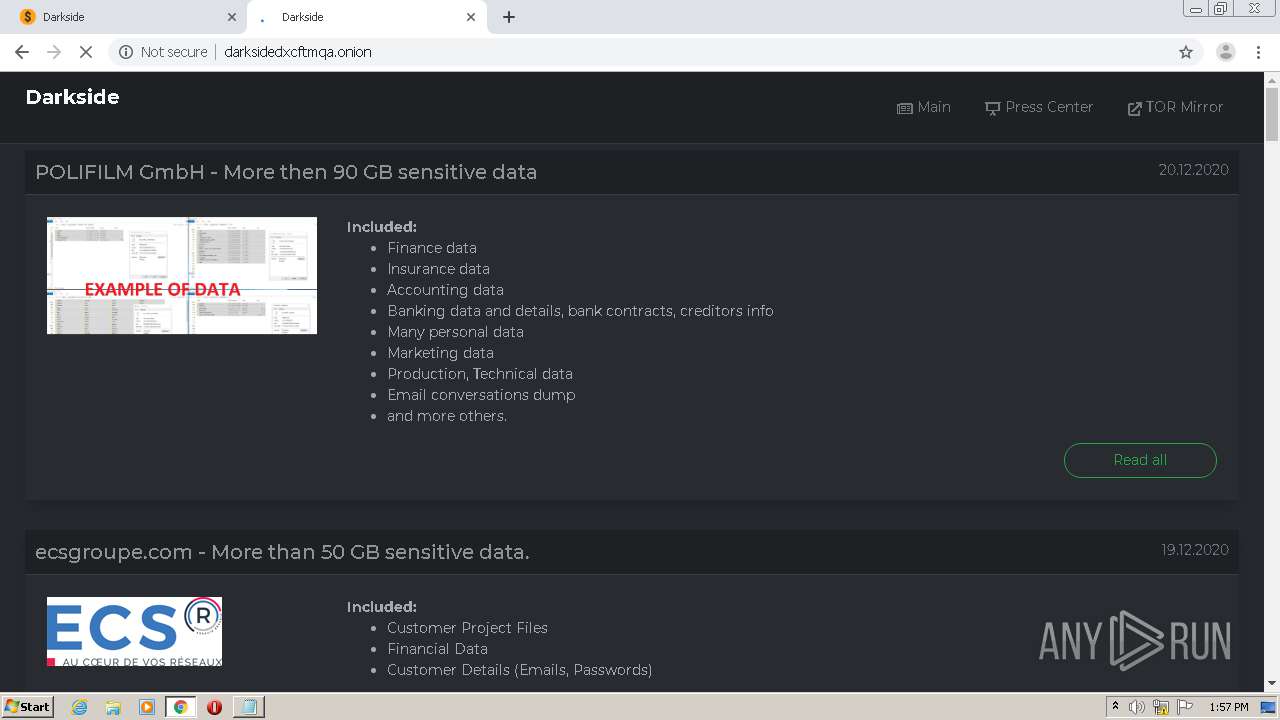
Fig. 24: DarkSide blog about victims - ‘Hall of Shame’
And finally, there was one unusual option on DarkSide website. Registration for press and for recovery teams/companies. The DarkSide operators provided them with non-public notifications and additional discounts and support for recovery. Well, Ransomware as a Service with customer support…
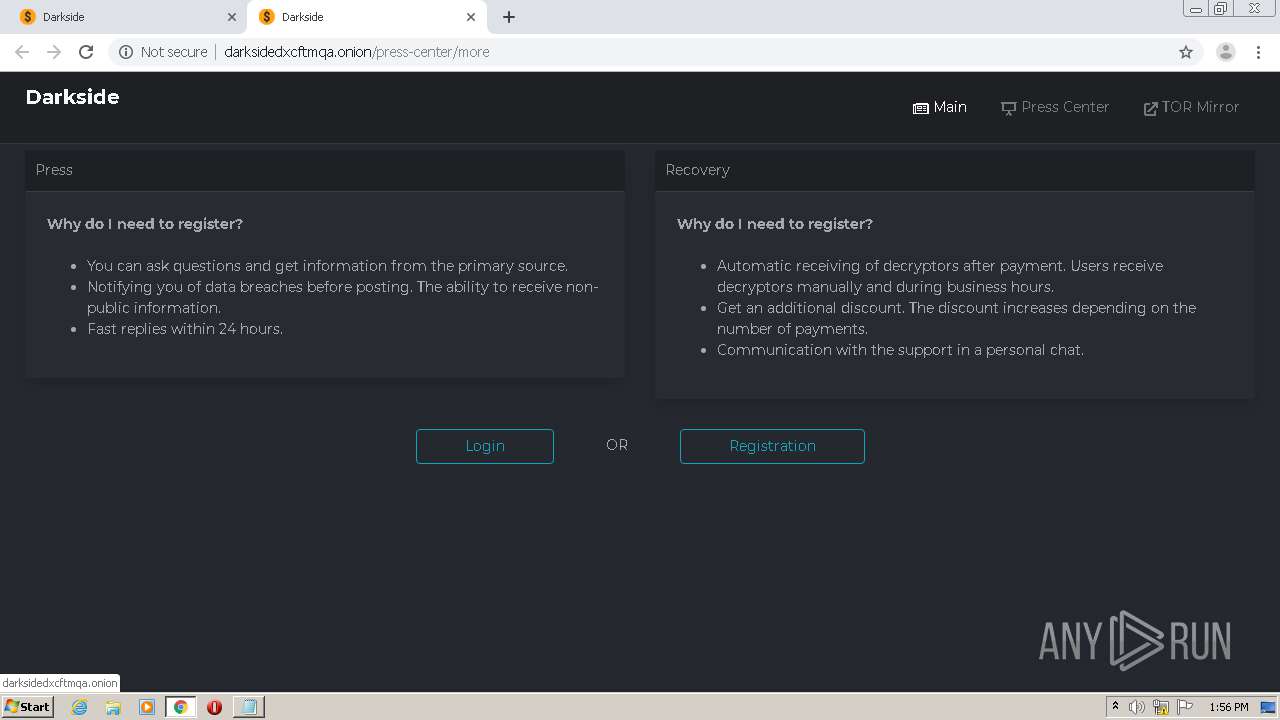
Fig. 25: DarkSide blog about victims - ‘Hall of Shame’
Conclusion
In this article we briefly analyzed some features of DarkSide ransomware such as performing checks for supported/allowlisted languages and keyboards and some packing options. Then, we discussed its configuration, cryptography and ransomnotes and we compared them with Revil/Sodinokibi ransomware family. It turns out that there are similarities between those two ransomware families.
Next, based on our research of ransomware samples and collected ransomnotes we summarize and provided examples of DarkSide victims and categories of leaked data. Finally, we pointed out two interesting cases, one with signed ransomware samples and one analysis with DarkSide website walkthrough.
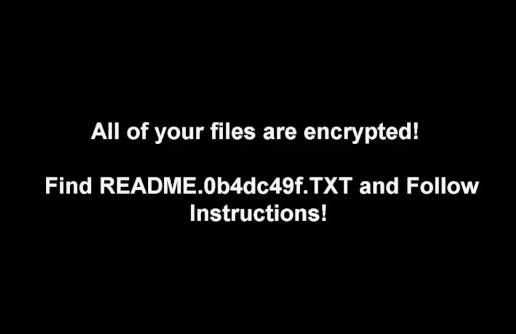
Fig. 26: Computer infected with DarkSide ransomware
References
- FBI Statement on Compromise of Colonial Pipeline Networks
- US fuel pipeline hackers ‘didn’t mean to create problems’ - BBC post
- FireEye Threat Research about DarkSide Ransomware
- REvil Ransomware Analysis by Intel471
- Hybrid Analysis with obfuscated PowerShell command spawned
- DarkSide Ransomware Links to REvil Group Difficult to Dismiss - Flashpoint research
- Bloomberg: Colonial Hackers Stole Data Thursday Ahead of Shutdown
Any.Run samples and analyses
Disclaimer: Most of the ransomnotes screenshots and DarkSide portal have been taken from Any.Run analysis linked below
- https://app.any.run/tasks/47fea7e6-fc3a-4bdf-a555-6bd5571b2212/ (Revil)
- https://app.any.run/tasks/997b38da-6963-4f3b-b79e-ee8cd8640342/
- https://app.any.run/tasks/303baf96-4254-4eb8-9db7-439fe8b0288f/
- https://app.any.run/tasks/1866ce60-8d27-423c-a504-f92374a04704/
- https://app.any.run/tasks/7582ad6a-495f-4263-9eac-f0370901f069/
- https://app.any.run/tasks/1148ab39-b71a-430c-bfe2-8fcb8a7f5b38/
- https://app.any.run/tasks/2487ff59-5631-4a92-862b-92691049e8fd/
- https://app.any.run/tasks/24ceaab6-3b5e-43e4-a85f-0c3b52f5930b/
- https://app.any.run/tasks/57a74ef4-8260-4aec-b676-8d808d9dad48/
- https://app.any.run/tasks/fcf06ca7-bd65-49e9-9401-e5838e182aa3/
- https://app.any.run/tasks/a5692a77-954f-4110-9861-05a08a00d8f5/
- https://app.any.run/tasks/78dd636b-66c8-454c-8eaa-d4de19bd5baf/
- https://app.any.run/tasks/88229240-0b19-4b29-ae0c-decb4501f57c/