In March 2021 our researchers discovered APT campaign targeting Slovakia. We found that this campaign has been active at least since February 2021 and some C&C servers were still active in June 2021. Threat actor used mostly Cobalt Strike and phishing emails and documents on behalf of Slovak National Security Authority. Our threat intelligence and malware research revealed several command and controls servers around the globe. Some of them had direct relations to targets in Slovak republic.
Cobalt Strike
As described on the Cobalt Strike’s website, Cobalt Strike is “software for Adversary Simulations and Red Team Operations”. It is a commercial tool with price $3,500 per user for one year and it is used by many pentesters and red teamers as well as by some of the advanced threat actors such as APT19, APT29, APT32, Leviathan, Cobalt Group and FIN6. Again, official website says:
“Cobalt Strike gives you a post-exploitation agent and covert channels to emulate a quiet long-term embedded actor in your customer’s network”.
Therefore it is kind of more interesting malware than relatively common backdoors, rats and Metasploit and other publicly accessible free samples.
“NSA” ISO Sample
Somebody submitted the sample called AktualizC!ciu.img to the sandbox Any.Run on 23rd March 2021. This sample was been submitted for analysis from Slovakia. And then, it has been submitted again on 9th April. Probabably someone was already/again investigating the attack. The original ISO filesystem contains timestamps with information about the timezone: UTC-07:00 (Pacific Daylight Time). Also, this sample has been submitted to VirusTotal shortly after the reported timestamps of creation the ISO filesystems. This indicates that no tampering of creation timestamps of ISO filesystem has been applied.
The Volume name of the ISO filesystem is interesting - it contains “NBU”, which is abbreviation of the National Security Authority in Slovakia.
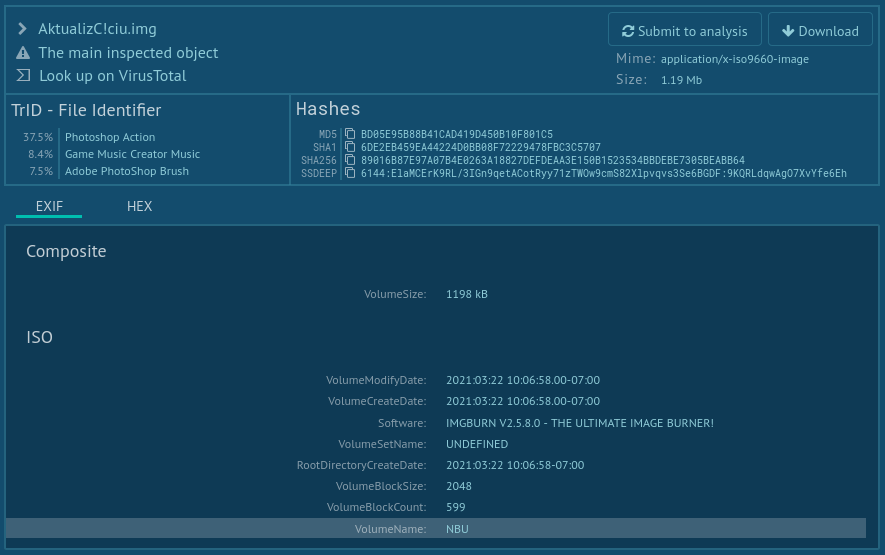
Fig. 1: NSA ISO Sample
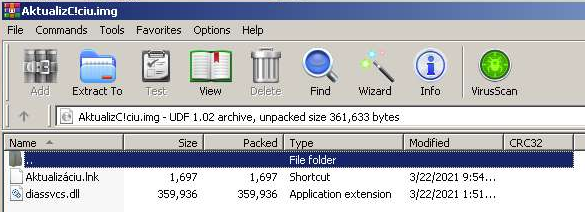
Fig. 2: Content of NSA ISO Sample
The “NSA” ISO Sample contains two files: one LNK file and one DLL file. The LNK file actually executes the following command:
C:\Windows\System32\rundll32.exe diassvcs.dll InitializeComponent
Refering the access time of LNK file, this file has been accessed 13 minutes before the ISO filesystem has been created. Thus there is probably no automation in the packaging process of the malware sample and the payload for delivery (see below) has been created manually by human.
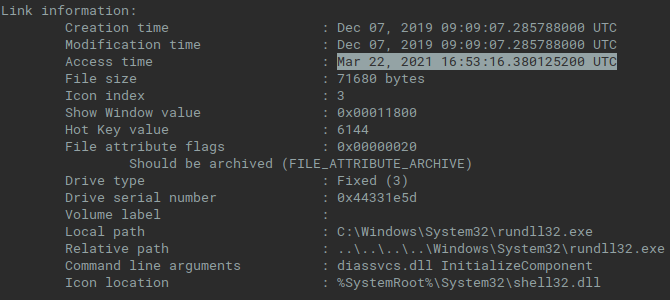
Fig. 3: Details of LNK file from NSA ISO Sample
Cobalt Strike Beacon
DLL file diassvcs.dll is a loader/packer with some anti-analysis protections enabled. In the picture below there is the unpacking routine consisting of decryption loops followed by the calls to VirtualProtect Windows API and to the unpacked payload itself.
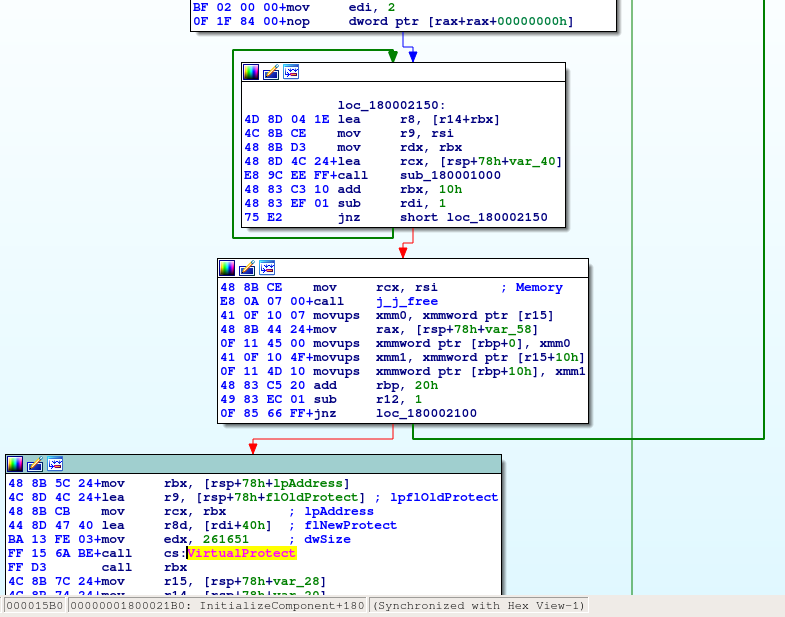
Fig. 4: Unpacking routine of DLL Loader from NSA ISO Sample
The unpacked payload is DLL file, but without standard MS-DOS header. This malformed header can be often seen for example in Metasploit’s Meterpreter payloads and it is used as a part of shellcode.
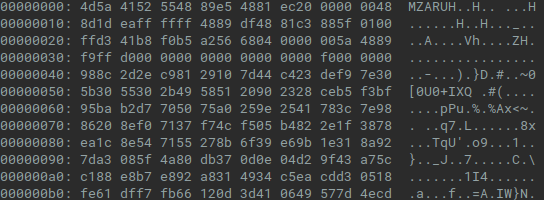
Fig. 5: Malformed MZ header of unpacked Cobalt Strike Beacon
This DLL file is actually a Cobalt Strike Beacon. The extracted configuration is attached below.
BeaconType - HTTPS
Port - 443
SleepTime - 45000
MaxGetSize - 1403644
Jitter - 37
MaxDNS - Not Found
PublicKey - b'0\x81\x9f0\r\x06\t*\x86H\x86\xf7\r\x01\x01\x01\x05\x00\x03\x81\x8d\x000\x81\x89\x02\x81\x81\x00\xbf\x91i\x8e\xb3\x1dY\xcdH\xa2\x17\x1f\x7f\xb9j\x8b\x8f\xccY\xbd+\t\x1f\x9c\x9c\xc7\x0b\xff\x06\xbe\n/Q7\xf3ZQ6m\xc9\xc3A%n\xb2vdsA\xdc\xa0D\x93\xd5\x9e\xe6\x15-\xa0\x13/.@\xda\xf4\xf7q\xf3y\x84\xf3b!\x9fw\xf4\xf6D\xb5\xe7w\x19\x17\xe60&\x10\xb4]\xe7\xed\xa9\xbb`&1\xfc\xbe/\x1c\xaaJ3\x8d\x86\x93\x1c\x15\x9e\x94\xd1\x9f\x93\xab\xb9\x93\xe9w\x94\t\xef\xa2Z\xed\xc8\x12\xd0\xdd\x02\x03\x01\x00\x01\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00'
C2Server - content.pcmsar.net,/jquery-3.3.1.min.js
UserAgent - Not Found
HttpPostUri - /jquery-3.3.2.min.js
HttpGet_Metadata - Not Found
HttpPost_Metadata - Not Found
SpawnTo - b'\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00'
PipeName - Not Found
DNS_Idle - Not Found
DNS_Sleep - Not Found
SSH_Host - Not Found
SSH_Port - Not Found
SSH_Username - Not Found
SSH_Password_Plaintext - Not Found
SSH_Password_Pubkey - Not Found
HttpGet_Verb - GET
HttpPost_Verb - POST
HttpPostChunk - 0
Spawnto_x86 - %windir%\syswow64\dllhost.exe
Spawnto_x64 - %windir%\sysnative\dllhost.exe
CryptoScheme - 0
Proxy_Config - Not Found
Proxy_User - Not Found
Proxy_Password - Not Found
Proxy_Behavior - Use IE settings
Watermark - 1359593325
bStageCleanup - True
bCFGCaution - False
KillDate - 0
bProcInject_StartRWX - False
bProcInject_UseRWX - False
bProcInject_MinAllocSize - 17500
ProcInject_PrependAppend_x86 - b'\x90\x90'
Empty
ProcInject_PrependAppend_x64 - b'\x90\x90'
Empty
ProcInject_Execute - ntdll:RtlUserThreadStart
CreateThread
NtQueueApcThread-s
CreateRemoteThread
RtlCreateUserThread
ProcInject_AllocationMethod - NtMapViewOfSection
bUsesCookies - True
HostHeader -
From this config we can see that this is a HTTP Beacon based on jQuery Malleable-C2 profile
Cobalt Strike C2 Server
Analysis of Cobalt Strike C2 Server at content.pcmsar[.]net revealed couple of interesting things. The server is hosted at Canadian OVH SAS hosting. It is powered by nginx webserver, with Let’s Encrypt certificate issued on Mar 15 08:27:41 2021 GMT (approximately one week before the Cobalt Strike Payload packed into ISO). Without any parameters, the HTTP requests are redirected to https://spectator.sme.sk/, a popular Slovakia’s English-language online newspaper.
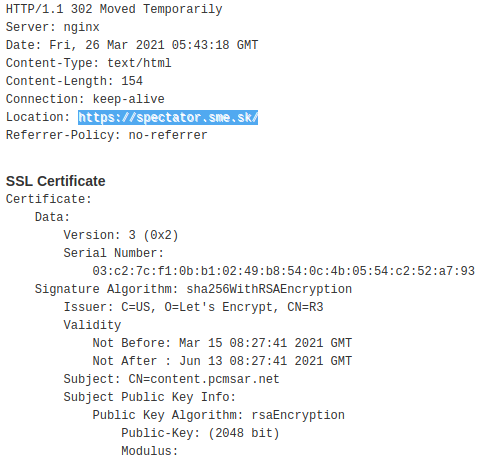
Fig. 6: HTTPS details of Cobalt Strike C&C server
Threat Actor C2 Infrastructure
Based on observations above (and couple of others) there is possible to discover more C2 servers. Some of them are hosted in OVH, and many of them have SSL/TLS certificates issued by Sectigo instead of Let’s Encrypt. They are active since February 2021 (confirmed), but probably some of them was used also back in 2020. These C2 servers also incorporated the redirection to innocent websites and they uses similar domains by themselves. For example, C2 server hosted at cbdnewsandreviews[.]net redirects visitors to https://www.newsreview.com//.
The discovered C2 servers are located around the globe, for example, in Canada, France and Australia.
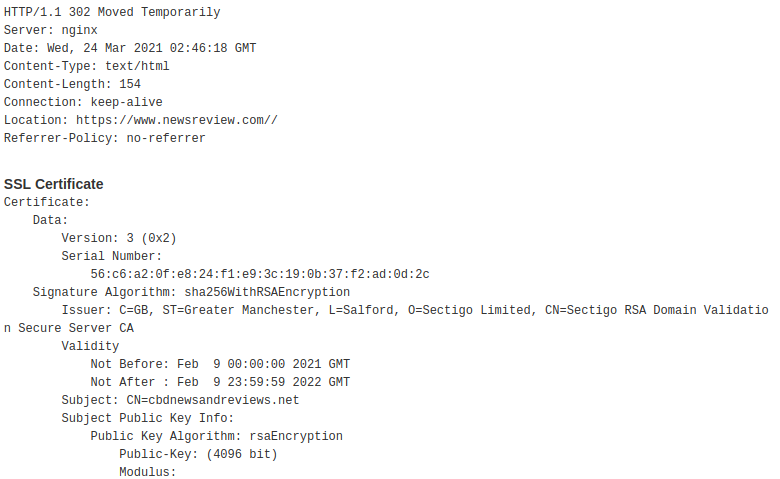
Fig. 7: HTTPS details of another Cobalt Strike C&C server
More Malware Samples
With information about C2 infrastructure, our researchers have found another malware samples linked to the same threat actor. For example, another ISO called evil.iso. This file is very similar to the analyzed “NSA” ISO, it contains LNK and DLL file with Cobalt Strike Beacon payload. It was submitted to Any.Run on 26th February 2021 from Netherlands (hypothesis is that the malware analyst used the ProtonVPN which is often used by them for protecting their privacy). First submittion on VirusTotal is from 25th February, however, the ISO file (with original name invitation.iso) was created most likely on 17th February in Pacific Standard Timezone (UTC-08:00).
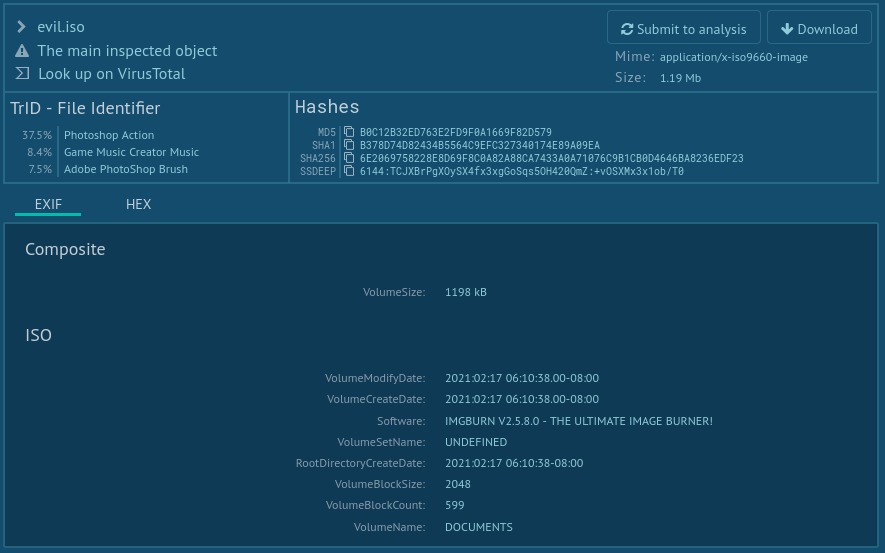
Fig. 8: Evil ISO Sample
Delivery Method
Based on similarities of analyzed ISO files we were able to find another similar files. It seems that at least some of them have been delivered via phishing emails with ISO/IMG attachments looking like Word documents. Moreover, it seems that the same threat actor delivers at least one phishing email to the targets in Czech republic in March 2021.
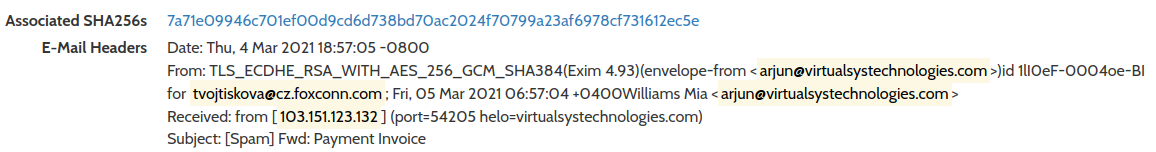
Fig. 9: Example of email with similar attachement delivered to the private company
Findings and Summary
We were able to discover and track the campaign targeting Slovakia Government and Cobalt Strike infrastructure used by the threat actor. This analysis was based solely on publicly available information, community threat intelligence sources and our own malware research. The incident and results have been reported to the local authorities such as computer security incident response team. The report included the collected indicators of compromise such as hashes and IP addresses. These IOCs have been used during the investigation. Imagine, it is like the oraculum - you can predict which IP addresses will the attacker use in the next steps, or, you can use the reported IOCs as a pivots during the forensic analysis. All the results are only from the hunting in public sources.
DEF CON Talk

Fig. 10: Our talk at DEFCON 29 Recon Village
We presented this case at Recon Village at DEF CON 29 conference in August 2021 (Las Vegas & Virtual). We also introduced and explained couple of concepts, tips and tricks for malware hunting and advanced search. Presentation slides and video from our talk are available below.
Afterword
(updated on Sep 13, 2021)
This blog post was originally based on research and analysis during March and April 2021. Therefore, we published our results based only on data available at that time, without referring to the results and articles published a few weeks and months later.
Few days after DEF CON talk and after publishing this blog post, Slovak technology portal Zive.sk wrote an article about this incident based on our research. Then, ESET Research found that this attack targeted diplomats from more than 13 European countries and think-tanks and this attack was linked to APT29/Dukes/Nobelium also by Microsoft Threat Intelligence Center. In their article from the end of May they published IOCs which contain also some of the IOCs mentioned here, including “NSA” ISO Sample.
And finally, Catalin Cimpanu from The Record published post “Russian cyberspies targeted the Slovak government for months” based on above work.
Sample IOCs
Hashes
- bd05e95b88b41cad419d450b10f801c5: AktualizC!ciu.img
- ed24b708a0abb91d2d984c646527823f: Aktualizáciu.lnk
- e55d9f6300fa32458b909fded48ec2c9: diassvcs.dll
- 1adfe420043628286d0f3ff007113bfa: Cobalt Strike Beacon
- b0c12b32ed763e2fd9f0a1669f82d579: evil.iso
- 038579bdb1de9e0ab541df532afeb50d: Programme outline.lnk
- 72b494d0921296cdd5e4a07a0869b244: Plending forms.lnk
- 600aceaddb22b9a1d6ae374ba7fc28c5: GraphicalComponent.dll
Domains
- content.pcmsar[.]net
- cbdnewsandreviews[.]net
IP Addresses
- 51.79.69[.]211
- 139.99.167[.]177
References
- https://www.cobaltstrike.com/
- https://app.any.run/tasks/2c77358b-a7bc-4ebc-b034-362a1ddd0cd3/
- https://www.virustotal.com/gui/file/89016b87e97a07b4e0263a18827defdeaa3e150b1523534bbdebe7305beabb64/details
- https://www.cobaltstrike.com/help-malleable-c2
- https://github.com/threatexpress/malleable-c2
- https://app.any.run/tasks/41080dd6-5e6d-4150-8fab-715f142a9d7e/
- DEF CON 29 Recon Village Presentation Slides
