Introduction
Netsh, in its full name Network Shell, is a command-line tool, for listing and configuring various network settings. Configuration is possible locally or remotely. Netsh has been available on Microsoft operating systems since the release of Windows 2000. In a simple definition, Netsh would represent an interface between the user and the operating system, that allows configuration of network settings. A huge advantage of Netsh is that administrative tasks can be set up by running scripts.
Netsh Context
Netsh utilizes several DLL (Dynamic-Link-Library) files to interact with operating system components, each of which provides a different extension called context. A context can be understood as a set of commands, specific to individual implementations in the network. For example, the Dhcpmon.dll library is the library that allows Netsh to configure and manage DHCP servers.
After starting the command line and typing the netsh command, it is possible to display a list of contexts, using the question mark ?.
C:\Users\ASUS>netsh
netsh>?
The following commands are available:
Commands in this context:
.. - Goes up one context level.
? - Displays a list of commands.
abort - Discards changes made while in offline mode.
add - Adds a configuration entry to a list of entries.
advfirewall - Changes to the `netsh advfirewall' context.
alias - Adds an alias.
bridge - Changes to the `netsh bridge' context.
bye - Exits the program.
commit - Commits changes made while in offline mode.
delete - Deletes a configuration entry from a list of entries.
dhcpclient - Changes to the `netsh dhcpclient' context.
dnsclient - Changes to the `netsh dnsclient' context.
dump - Displays a configuration script.
exec - Runs a script file.
exit - Exits the program.
firewall - Changes to the `netsh firewall' context.
help - Displays a list of commands.
http - Changes to the `netsh http' context.
interface - Changes to the `netsh interface' context.
ipsec - Changes to the `netsh ipsec' context.
lan - Changes to the `netsh lan' context.
mbn - Changes to the `netsh mbn' context.
namespace - Changes to the `netsh namespace' context.
netio - Changes to the `netsh netio' context.
offline - Sets the current mode to offline.
online - Sets the current mode to online.
p2p - Changes to the `netsh p2p' context.
popd - Pops a context from the stack.
pushd - Pushes current context on stack.
quit - Exits the program.
ras - Changes to the `netsh ras' context.
rpc - Changes to the `netsh rpc' context.
set - Updates configuration settings.
show - Displays information.
trace - Changes to the `netsh trace' context.
unalias - Deletes an alias.
wcn - Changes to the `netsh wcn' context.
wfp - Changes to the `netsh wfp' context.
winhttp - Changes to the `netsh winhttp' context.
winsock - Changes to the `netsh winsock' context.
wlan - Changes to the `netsh wlan' context.
The following sub-contexts are available:
advfirewall bridge dhcpclient dnsclient firewall http interface ipsec lan mbn namespace netio p2p ras rpc trace wcn wfp winhttp winsock wlan
To view help for a command, type the command, followed by a space, and then type ?.
Common problems solved with Netsh
One of the most common problems, that a standard user can experience is inability to connect to a website. This error is shown below, in the image:
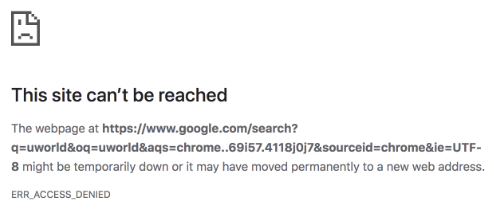
Figure 1 - Preview of “This site can’t be reached” error
There are several ways to solve such a problem. Many websites or forums advise, for example, reinstalling the Google Chrome browser or resetting Google settings to default. There are more options, but one of them is to use Network Shell, which can reset the so-called Winsock Catalog to default settings using a short command. Winsock is an API on the Windows operating system, that handles input/output requests, between web applications in a browser and an end devices. So, catalog is a database that stores settings. In the Windows operating system, data about namespace providers¹ are stored in the database, which mediate the map, between Winsock and systems such as DNS. The second object, that is stored in the database, is information about Internet protocols, such as TCP/IP. Due to the fact that the Winsock Catalog may contain incorrect data, the above-mentioned error most often occurs when loading the page. With the netsh winsock reset command, the entire database can be reset to default settings, which will solve the problem and load the page quickly.
The second most used command in troubleshooting is netsh int ip reset. This is a command, which will restart the TCP/IP stack. This step is recommended if browsing through internet is slow, or there is a problem with a stable Internet connection after performing an operating system update. The command replaces the TCP/IP and DHCP configurations in the registry and restores them to default. This means, for example, removing all static IP addresses for all network interfaces. After this command, it is necessary to perform a complete restart of the device and reconfiguration of the network.
Scenarios and network monitoring
A scenario is a predefined set of options, that are used for monitoring and troubleshooting network. After entering the netsh trace show scenarios command, all available scenarios will be displayed.
netsh>trace show scenarios
Available scenarios (23):
-------------------------------------------------------------------
AddressAcquisition : Troubleshoot address acquisition related issues
AddressAcquisitionServer : Troubleshoot address acquisition server related issues
DirectAccess : Troubleshoot DirectAccess related issues
DirectAccessServer :
FileSharing : Troubleshoot common file and printer sharing problems
InternetClient : Troubleshoot web connectivity issues
InternetServer : Troubleshoot server-side web connectivity issues
L2SEC : Troubleshoot layer 2 authentication related issues
LAN : Troubleshoot wired LAN related issues
Layer2 : Troubleshoot layer 2 connectivity related issues
MBN : Troubleshoot mobile broadband related issues
NDIS : Troubleshoot network adapter related issues
NetConnection : Troubleshoot network connection related issues
NetworkSnapshot : Collect the current network state of the system
P2P-Grouping : Troubleshoot Peer-to-Peer Grouping related issues
P2P-PNRP : Troubleshoot Peer Name Resolution Protocol (PNRP) related issues
RemoteAssistance : Troubleshoot Windows Remote Assistance related issues
Virtualization :
VPNServer : Troubleshoot VPN related issues
WCN : Troubleshoot Windows Connect Now related issues
WFP-IPsec : Troubleshoot Windows Filtering Platform and IPsec related issues
WLAN : Troubleshoot wireless LAN related issues
XboxMultiplayer : Troubleshoot Xbox Live Multiplayer connectivity-related issues
As an example, we can run a scenario designed for problems with wireless network, with the command netsh trace start scenario = wlan. However, started monitoring and collecting traces will not turn off automatically. It can be turned off with the netsh trace stop command run from command line with administrator privileges. After the process is completed, it takes some time for the data to be collected and evaluated.
netsh>trace start scenario = wlan
Trace configuration:
-------------------------------------------------------------------
Status: Running
Trace File: C:\Users\ASUS\AppData\Local\Temp\NetTraces\NetTrace.etl
Append: Off
Circular: On
Max Size: 512 MB
Report: Off
netsh>trace stop
Merging traces ... done
Generating data collection ... done
The trace file and additional troubleshooting information have been compiled as "C:\Users\ASUS\AppData\Local\Temp\NetTraces\NetTrace.cab".
File location = C:\Users\ASUS\AppData\Local\Temp\NetTraces\NetTrace.etl
Tracing session was successfully stopped.
As shown in the block above, the process will generate a .cab directory, that contains several files with information, that can greatly help in finding network problems. These are, for example, DNS reports, network settings, connection speed or stability, or the encryption algorithm used during data transmission over the network.
An alternative for WLAN troubleshooting is the netsh wlan show wlanreport command, the advantage of which is generated clear html file.
netsh>wlan show wlanreport
Generating report ...
Querying WLAN Events ...
Querying NCSI Events ...
Querying NDIS Events ...
Querying EAP Events ...
Querying WCM Events ...
Querying Kernel Events ...
Querying System Events ...
Running ipconfig ...
Running netsh wlan show all ...
Querying Wireless Profiles ...
Querying System and User Certificates ...
Querying User Info ...
Querying Network Devices ...
Report written to: C:\ProgramData\Microsoft\Windows\WlanReport\wlan-report-latest.html
done.
The report contains the following information:
- Wi-Fi graph - summary. The graph shows all internet connections, that have been recorded. By clicking, you can view each connection separately and read information, such as the length of the connection, the specific time, or the reason for the connection loss. Red points indicate an error, after clicking on it, the page will move to information about reason of the error that occurred.
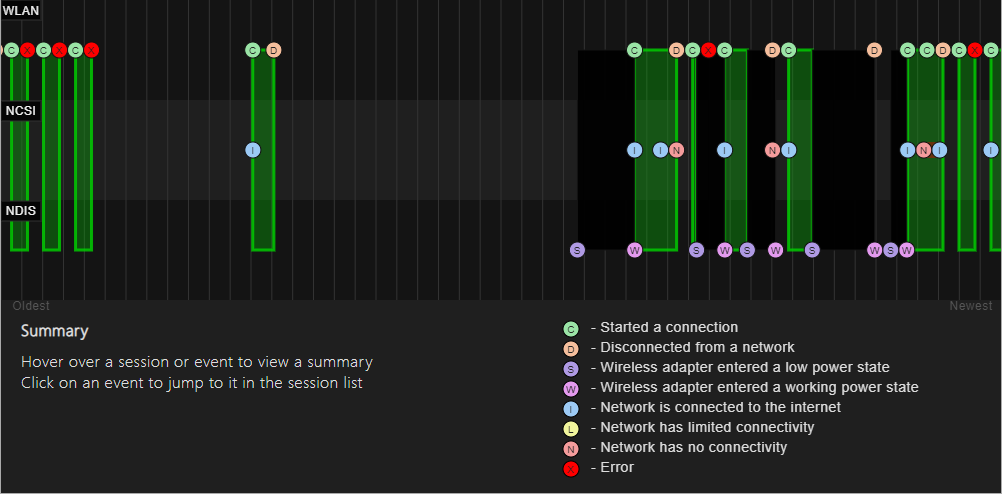
Figure 2 - Wi-Fi summary graph
- Report information. When was the report created and how many days does it cover.
- General information about the system. Includes information such as device name, BIOS version, device ID.
- Information about the logged-in user.
- Network adapters. The report contains detailed information about all network adapters on the given PC.
- Script output. This part contains displayed output of following commands:
- ipconfig/all
- netsh wlan show all
- certutil -store -silent My & certutil –store –silent –user My
- Profile Output
- Summary
- Summary of successful, failed connections and connections with warning.
- Duration of connection
- Disconnect Reasons
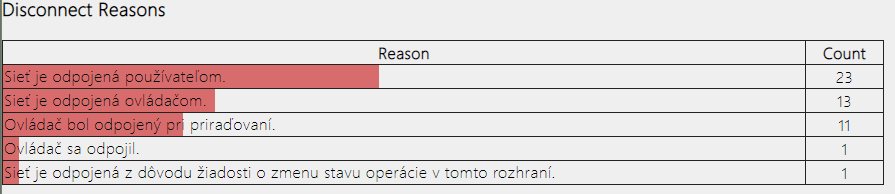
Figure 3 - Disconnect Reasons
- Information about connecting to Wi-Fi. Detailed information related to each wireless connection. Names of interfaces, profile, SSID, reason for disconnection, etc. This information is linked to the graph and to the individual labels in it.
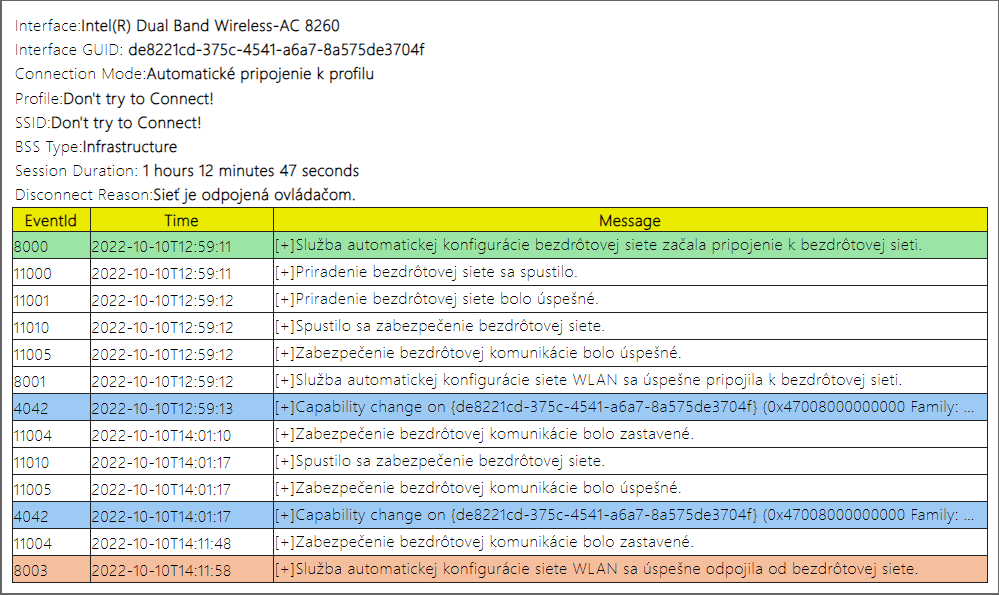
Figure 4 - Table of connection events
Security threads
Since, Network Shell offers many commands, some of them can help the attacker in his intentions. Let’s assume, that an attacker has gained access to a device, either through an infected USB, social engineering, or physical access to the device.
After running the command line “as an administrator”, it is possible to set up, change the rules or completely disable the firewall on the computer. Completely disabling the firewall would look like this:
C:\WINDOWS\system32>netsh firewall set opmode mode=disable
IMPORTANT: Command executed successfully.
However, "netsh firewall" is deprecated;
use "netsh advfirewall firewall" instead.
For more information on using "netsh advfirewall firewall" commands
instead of "netsh firewall", see KB article 947709
at https://go.microsoft.com/fwlink/?linkid=121488 .
Ok.
However, the question remains, what are the attacker’s intentions? If his intention is to perform a DoS attack, he can use Netsh, to make the device not connect to any website.
Figure 5 - “Unable to connect” screenshot
Specifically, all pages that run on HTTP and HTTPS protocols will be unable to load. This can be done by blocking ports 80 and 443 for the user.
C:\WINDOWS\system32>netsh advfirewall firewall add rule name="Block Ports" protocol=TCP dir=out remoteport=80,443 action=block
In case, that the attacker is trying to steal something, he can use Netsh to display every password of remembered WLANs in the device.
C:\WINDOWS\system32>netsh wlan show profile
C:\WINDOWS\system32>netsh wlan show profile WiFi-Name(SSID) key=clear
You need to look for the Security settings paragraph in the output, where the password of the given network is located.
Security settings
-----------------
Authentication : WPA2-Personal
Cipher : CCMP
Authentication : WPA2-Personal
Cipher : GCMP
Security key : Present
Key Content : ** password showed here **
In this way, an attacker can steal passwords for networks to which he would not have access normally because they are displayed in clear text format. That means, these network passwords, which may be corporate or personal, can be leaked through one device using the Netsh command.
